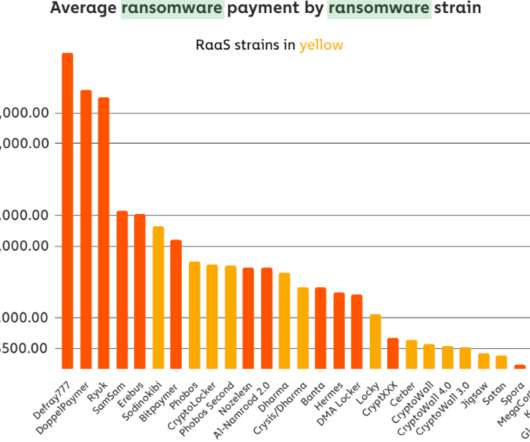
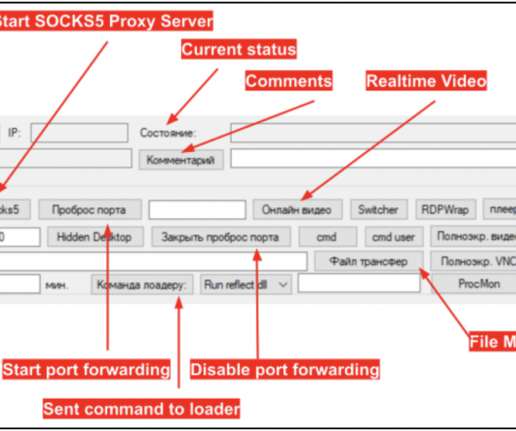
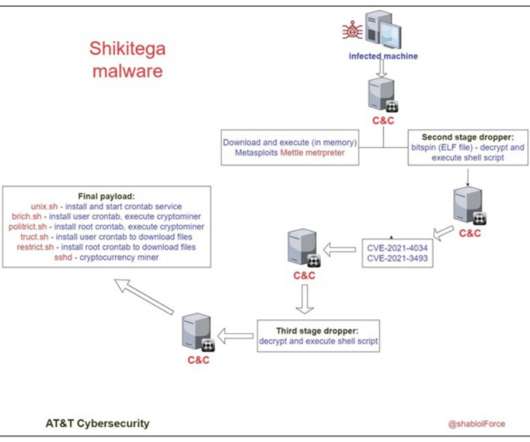
MY TAKE: A path for SMBs to achieve security maturity: start small controlling privileged accounts
The Last Watchdog
JUNE 23, 2021
Leading-edge cybersecurity systems in service today apply machine learning in some amazing ways to help large enterprises identify and instantly respond to cyber threats. The software giant’s intent was to make it more convenient and efficient for system administrators to perform Windows upkeep.











































Let's personalize your content