One Overlooked Element of Executive Safety: Data Privacy
CyberSecurity Insiders
JUNE 20, 2023
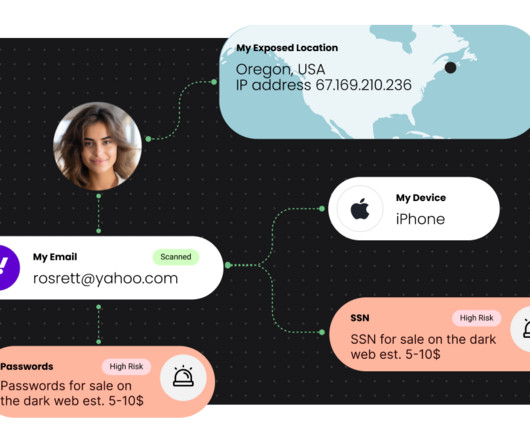
Executives also face risks from social media, where they are more visible and accessible than ever before. How to Protect Executive Data Privacy Clearly, none of this is optimal to executive productivity. Like the general public, executives can avoid oversharing personal information on social media.












































Let's personalize your content