Russia-linked APT28 uses COVID-19 lures to deliver Zebrocy malware
Security Affairs
DECEMBER 10, 2020
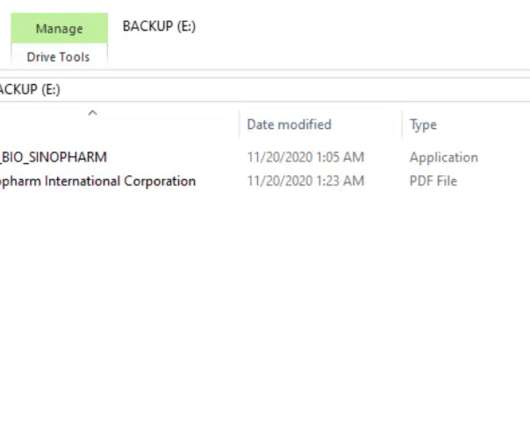
Russia-link cyberespionage APT28 leverages COVID-19 as phishing lures to deliver the Go version of their Zebrocy (or Zekapab) malware. Russia-linked APT28 is leveraging COVID-19 as phishing lures in a new wave of attacks aimed at distributing the Go version of their Zebrocy (or Zekapab) malware.

































Let's personalize your content