Home routers are being hijacked using vulnerability disclosed just 2 days ago
Malwarebytes
AUGUST 9, 2021
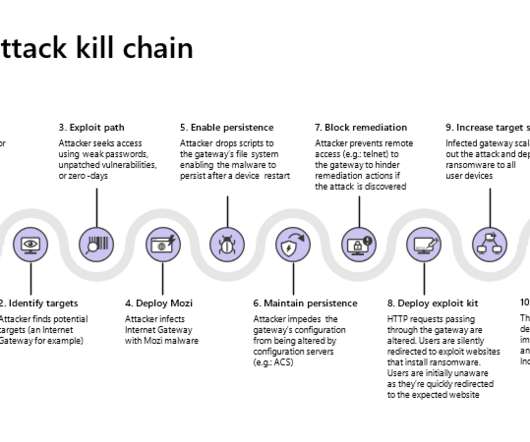
Router firmware. Under the description of CVE-2021-20090 you will find: “a path traversal vulnerability in the web interfaces of Buffalo WSR-2533DHPL2 firmware version <= 1.02 and WSR-2533DHP3 firmware version <= 1.24 The vulnerability is listed as CVE-2021-20090. Mitigation.








































Let's personalize your content