THE 11TH EDITION OF THE ENISA THREAT LANDSCAPE REPORT IS OUT!
Security Affairs
OCTOBER 19, 2023
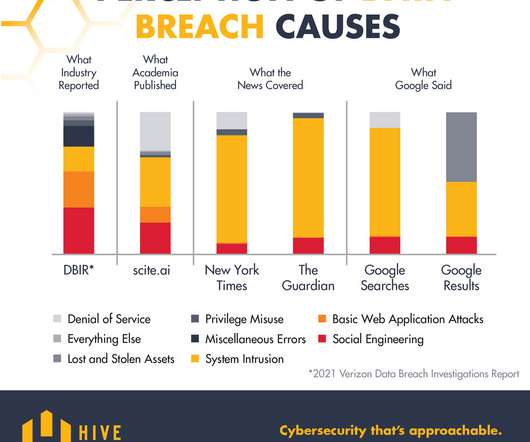
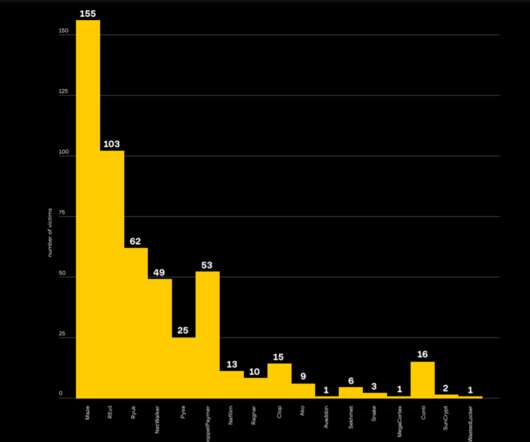
During the reporting period, key findings include: DDoS and ransomware rank the highest among the prime threats, with social engineering, data related threats, information manipulation, supply chain, and malware following.

























Let's personalize your content