No, Elon — X DDoS was NOT by Ukraine
Security Boulevard
MARCH 12, 2025
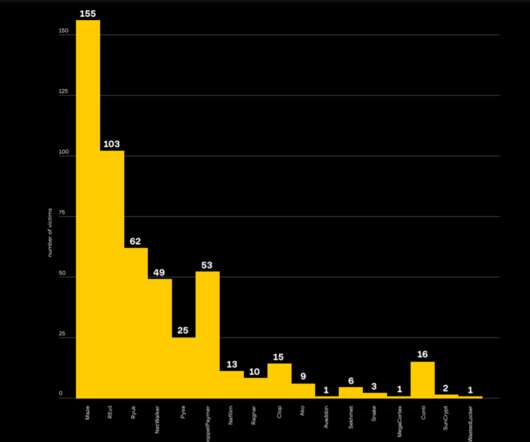
The post No, Elon X DDoS was NOT by Ukraine appeared first on Security Boulevard. X marks the botnet: Outage outrage was a Ukrainian cyberattack, implies our favorite African billionaire comedy villain.































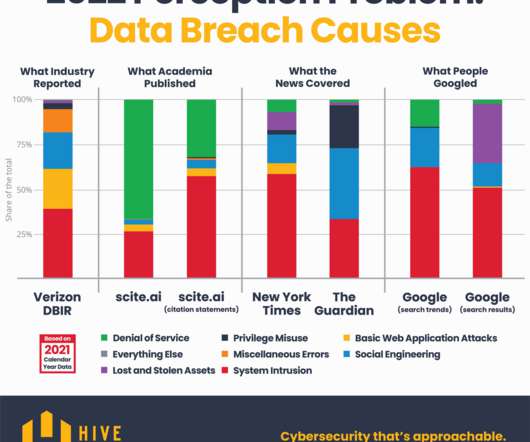
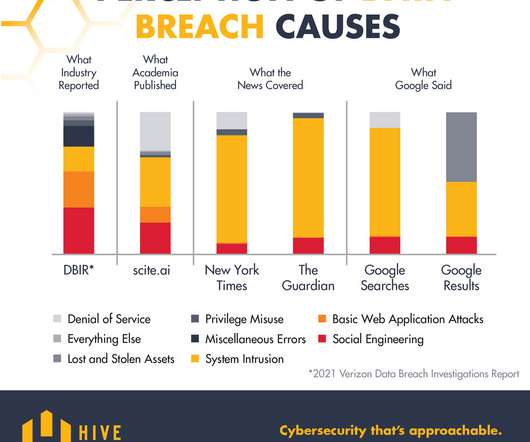


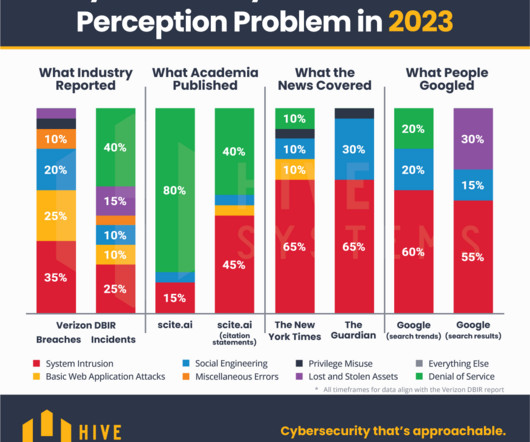

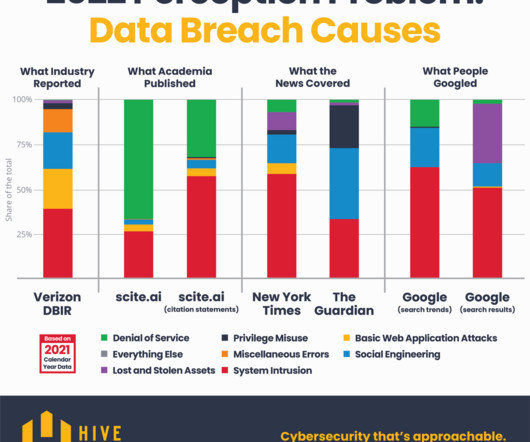









Let's personalize your content