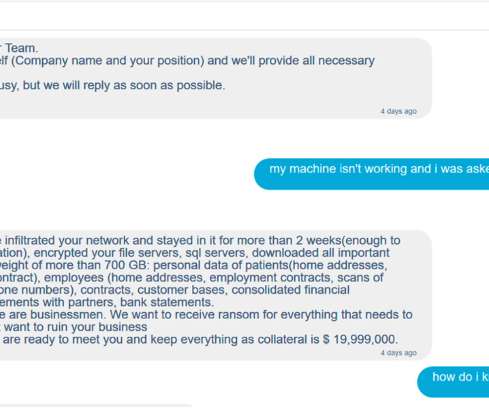
Healthcare organizations are a focus of ransomware attacks
Cisco Security
AUGUST 10, 2021
The adoption of electronic health records (EHRs) and even faster adoption of wireless medical devices and telemedicine has made patient information more accessible by more people. The shift to remote care and the widespread adoption of EHR solutions by health systems have shaped digital transformation in healthcare.



























Let's personalize your content