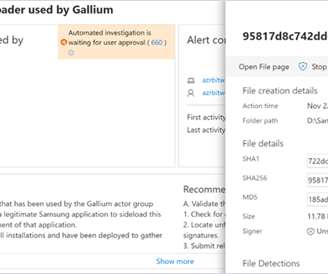
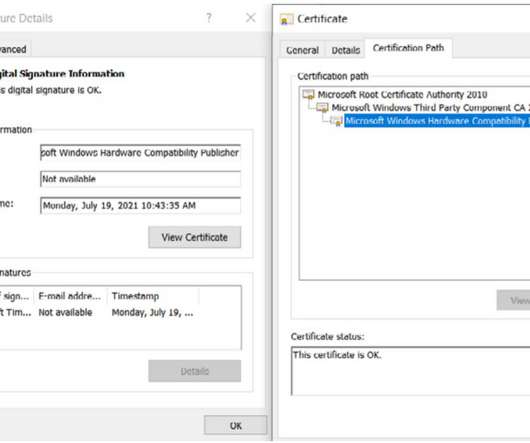
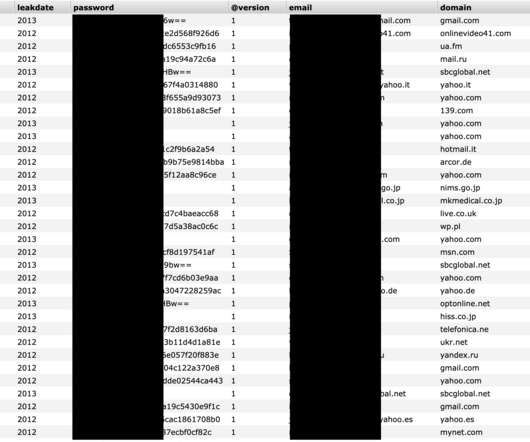
Over 92,000 Internet-facing D-Link NAS devices can be easily hacked
Security Affairs
APRIL 7, 2024
The flaw affects multiple D-Link NAS devices, including models DNS-340L, DNS-320L, DNS-327L, and DNS-325. The flaw impacts the following devices: DNS-320L Version 1.11, Version 1.03.0904.2013, Version 1.01.0702.2013 DNS-325 Version 1.01 DNS-327L Version 1.09, Version 1.00.0409.2013 DNS-340L Version 1.08


































Let's personalize your content