Information Security News headlines trending on Google
CyberSecurity Insiders
MAY 4, 2023
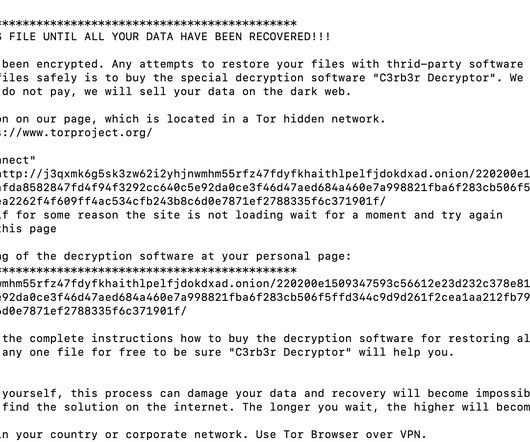
According to the advisory, all healthcare providers operating in the Indian subcontinent and in the whole of South Asia should be cautious about the said file-encrypting group that mainly targets the healthcare sector. The post Information Security News headlines trending on Google appeared first on Cybersecurity Insiders.





















Let's personalize your content