Supply Chain Attack Hits Password Manager
SecureWorld News
APRIL 27, 2021
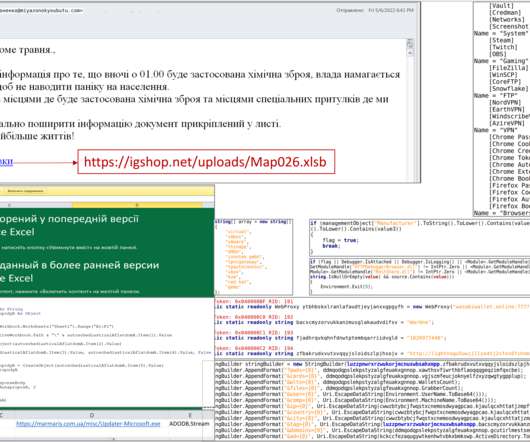
A similar type of attack just played out against an Enterprise Password Management tool called Passwordstate. Supply chain cyberattack against password manager Passwordstate. Affected customers' password records may have been harvested.". Manual Upgrades of Passwordstate are not compromised.








































Let's personalize your content