Download a banker to track your parcel
SecureList
DECEMBER 17, 2024
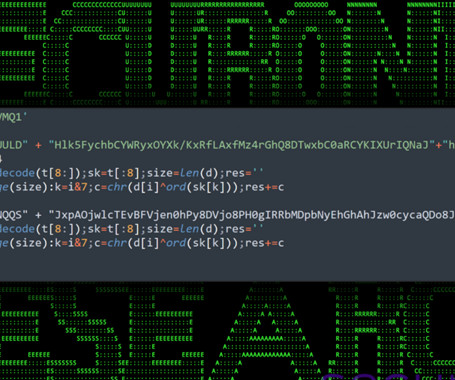
The link directed users to a phishing site offering to download Mamont for Android ( 12936056e8895e6a662731c798b27333 ). If the POST request returns a 200 code, the Trojan opens a window that supposedly downloads order details. Avoid downloading apps from anywhere but official sources.








































Let's personalize your content