Campaigns abusing corporate trusted infrastructure hunt for corporate credentials on ICS networks
SecureList
JANUARY 19, 2022
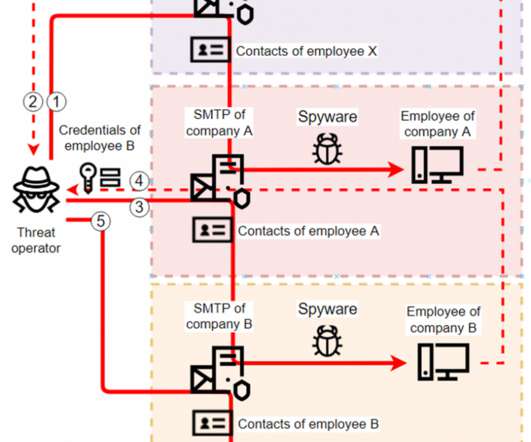
Kaspersky ICS CERT has uncovered a number of spyware campaigns targeting industrial enterprises. The attackers use off-the-shelf spyware, but limit the scope and lifetime of each sample to the bare minimum. The attackers use off-the-shelf spyware, but limit the scope and lifetime of each sample to the bare minimum.

















Let's personalize your content