New VPN Risk Report by Zscaler Uncovers Hidden Security Risks Impacting Enterprises
CyberSecurity Insiders
FEBRUARY 16, 2021
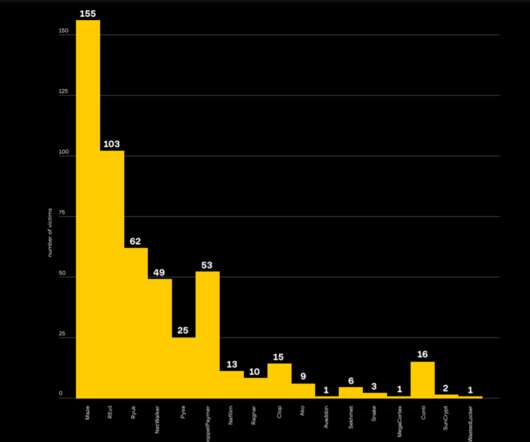
2021 Research Highlights Growing Security Vulnerabilities Around Targeted Social Engineering, Ransomware and Malware Attacks. To download the full study, see the Zscaler 2021 VPN Risk Report. For the last three decades, VPNs have been deployed to provide remote users with access to resources on corporate networks.












































Let's personalize your content