Author Q&A: Here’s why the good guys must continually test the limitations of ‘EDR’
The Last Watchdog
OCTOBER 30, 2023
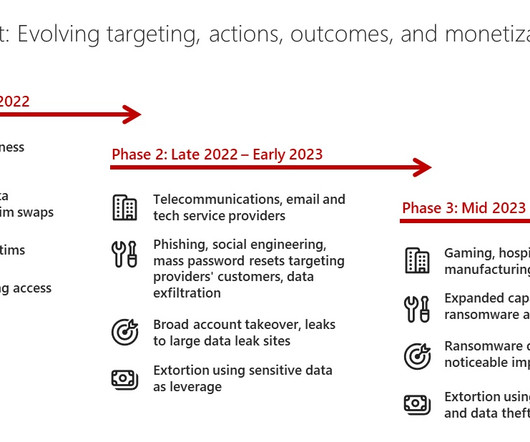
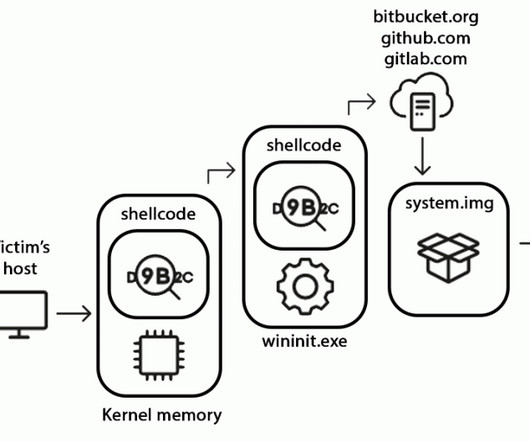
A new tier of overlapping, interoperable, highly automated security platforms must, over the next decade, replace the legacy, on-premise systems that enterprises spent multiple kings’ fortunes building up over the past 25 years. Related: How ‘XDR’ defeats silos Now along comes a new book, Evading EDR: The Definitive Guide for Defeating Endpoint Detection Systems , by a red team expert, Matt Hand, that drills down a premier legacy security system that is in the midst of this transitio






































Let's personalize your content