Vaccine Passports: Who, What, When, Where and How?
Lohrman on Security
MARCH 21, 2021

Security Boulevard
MARCH 21, 2021
The Federal Communications Commission’s (FCC) Public Safety and Homeland Security Bureau on March 12 identified five Chinese companies they said posed a threat to U.S. national security. These companies are: Huawei Technologies Co., ZTE Corp., Hytera Communications Corp., Hangzhou Hikvision Digital Technology Co. and Dahua Technology Co. The declaration, according to the FCC, is in.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CyberSecurity Insiders
MARCH 21, 2021
Just because you are running a small business doesn’t mean you are out of the reach of cybercriminals and hackers. In fact, small businesses are more susceptible to security breaches and cyberattacks because most often they dont expect the attack, thus are unprepared to handle the situation. Back in 2018, almost two-thirds of the small businesses suffered from cyber security attacks. .
Security Boulevard
MARCH 21, 2021
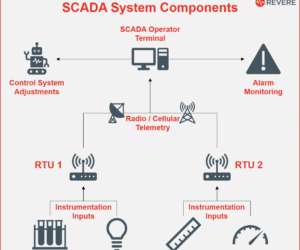
SCADA systems have been around since the early 1970s, way back when networks were all closed systems and hacking them was the stuff of spy movies. The post SCADA Security </br> in a Cellular World appeared first on FirstPoint. The post SCADA Security in a Cellular World appeared first on Security Boulevard.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Graham Cluley
MARCH 21, 2021
What do phone scammers who prey on the vulnerable deserve? Fart spray and glitterbombs, of course! A fun video makes some serious points, and could be a valuable lesson for your family and friends.

Security Boulevard
MARCH 21, 2021
It’s not surprising the COVID-19 pandemic that pushed workers home also accelerated cloud migration and digital transformation, but new research from Vectra.ai unearthed a troubling trend – 71% of Microsoft Office 365 deployments in medium to large companies suffered, on average, seven legitimate account takeovers at a time when remote workforces were more dependent than.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
Security Affairs
MARCH 21, 2021
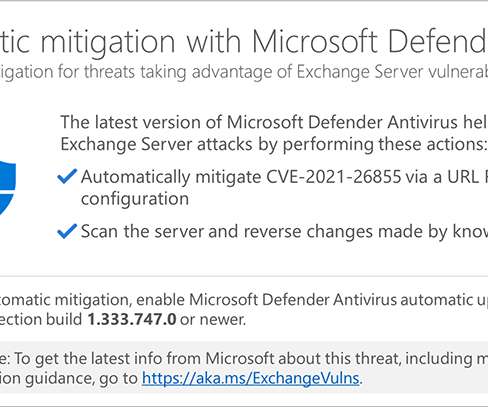
Microsoft announced that its Defender Antivirus and System Center Endpoint Protection now protects users against attacks exploiting Exchange Server vulnerabilities. Microsoft announced this week that Defender Antivirus and System Center Endpoint Protection now provide automatic protection against attacks exploiting the recently disclosed ProxyLogon vulnerabilities in Microsoft Exchange. “Today, we have taken an additional step to further support our customers who are still vulnerable and h

Bleeping Computer
MARCH 21, 2021
The printer fixing roller coaster continues as Microsoft is once again rolling out the KB5001649 out-of-band update to users via Windows Update. [.].

CyberSecurity Insiders
MARCH 21, 2021
This post was originally published by (ISC)² Management. A Day in the Life. Cybersecurity remains one of the most exciting technology jobs and one of the top sought-after positions by many technology professionals. It is also one of the most difficult positions for an employer to fill. Why is this the case? When you think about cybersecurity, the mind often drifts towards the good versus evil of technology.
Bleeping Computer
MARCH 21, 2021
With the release of the latest Windows 10 preview 'Dev' build, Microsoft is offering a glimpse at some of the new features and changes they are developing. Some of these features we love, while others not so much. Below we have outlined the new changes so that you can decide on your own. [.].

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

CyberSecurity Insiders
MARCH 21, 2021
Tesla Chief Elon Musk has cleared the air that if his company cars are being used for spying in china or anywhere else, then he would rather shut down the business than developing it. Speaking through a video link at the China Development Forum, the multi billionaire technologists reacted to the news that China has banned the use of Tesla cars for its military and government agency operations as the external cameras recording the footage on the said company automated vehicles where found sending
SecureBlitz
MARCH 21, 2021
This post will reveal how to control the aftermath of a data breach by using DRM for document security. Gathering both physical and digital evidence to correlate data from multiple sources to piece together a data breach incident is crucial in evaluating how and when the incident took place. The evidence can show if someone. The post Controlling Data Breach And The Use Of DRM For Document Security appeared first on SecureBlitz Cybersecurity.

Security Boulevard
MARCH 21, 2021
If there’s anything the past year has taught us is that connectivity is critical to business continuity. Not only businesses but governments and infrastructure services rely. The post How to assess </br> cellular network vulnerabilities appeared first on FirstPoint. The post How to assess cellular network vulnerabilities appeared first on Security Boulevard.

WIRED Threat Level
MARCH 21, 2021
DearCry is the first attack to use the same Microsoft Exchange vulnerabilities, but its lack of sophistication lessens the threat.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
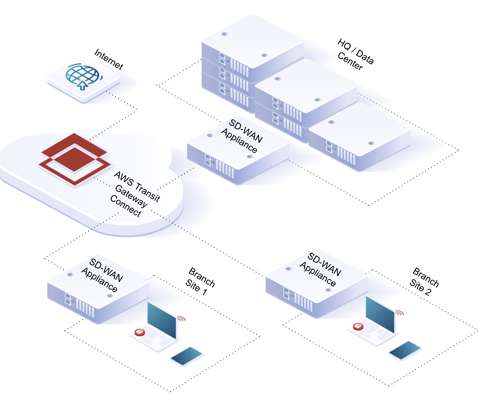
CyberSecurity Insiders
MARCH 21, 2021
This post was originally published by Amit Singh. As the only SASE platform built on a Polyscale public cloud architecture, Bitglass leverages AWS Transit Gateway Connect to seamlessly integrate with SD-WAN solutions. Traffic from branch routers is seamlessly routed to Bitglass for real-time security. This flexible, plug-and-play approach is markedly different from that of competitors, who are limited to specific SD-WAN partners for whom they build and maintain piecemeal integrations. .

Security Boulevard
MARCH 21, 2021
via the respected information security capabilities of Robert M. Lee & the superlative illustration talents of Jeff Haas at Little Bobby Comics. Permalink. The post Robert M. Lee’s & Jeff Haas’ Little Bobby Comics – ‘WEEK 321’ appeared first on Security Boulevard.

CyberSecurity Insiders
MARCH 21, 2021
The list of companies that have suffered a cyber attack on their Microsoft Exchange Servers seems to be ever expanding as the latest victim to fall prey is noted computing device maker Acer. The Taiwan-based company was hit by REvil ransomware, said Vital Kremez, the Intelligence CEO of the PC Giant. In what is known to our Cybersecurity Insiders, Acer’s domain servers were targeted by the group spreading REvil file encrypting malware to hackers and the malware is said to have hit the company on

Security Boulevard
MARCH 21, 2021
Many thanks to USENIX Enigma 2021 for publishing these outstanding conference videos on the YouTube USENIX Channel ; don't miss this erudite 27 video information & cybersecurity event. Permalink. The post USENIX Enigma 2021 – Mitch Negus’ ‘No Data, No Problem—Giving Nuclear Inspectors Better Tools Without Revealing’ appeared first on Security Boulevard.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.
Zero Day
MARCH 21, 2021
The vulnerabilities allowed attackers full and unfettered access to student PCs.

Security Affairs
MARCH 21, 2021
Department of Justice announced that Swiss hacker Till Kottmann, 21, has been indicted for conspiracy, wire fraud, and aggravated identity theft. A group of US hackers recently claimed to have gained access to footage from 150,000 security cameras at banks, jails, schools, healthcare clinics, and prominent organizations. Hackers also posted images captured from the hacked surveillance video on Twitter with an #OperationPanopticon hashtag, published images show that they have gained root shell ac

Security Boulevard
MARCH 21, 2021
Early on Thursday morning, March 18, 2021, I was posting content on LinkedIn when I glanced over at the top story in LinkedIn news that people were talking about in the U.S. I was intrigued when I saw the hottest comments coming in were on vaccine passports. But what shocked me even more was the. The post Vaccine Passports: Who, What, When, Where and How?
SecureBlitz
MARCH 21, 2021
Here, I will show you the essential cybersecurity tips to implement when working remotely (WFH). Not only international corporations and large enterprises are victims of cyberattacks. Cybercriminals are increasingly choosing smaller companies that have less advanced security systems and do not employ cybersecurity specialists. As a result, they are an easy target of attacks and.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Security Affairs
MARCH 21, 2021
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the international press subscribe here. Experts found 15 flaws in Netgear JGS516PE switch, including a critical RCE Google releases Spectre PoC code exploit for Chrome browser Google fixes the third actively exploited Chrome 0-Day since January NCSC is not aware of ransomware attacks compromising UK orgs th

Security Boulevard
MARCH 21, 2021
Many thanks to USENIX Enigma 2021 for publishing these outstanding conference videos on the YouTube USENIX Channel ; don't miss this erudite 27 video information & cybersecurity event. Permalink. The post USENIX Enigma 2021 – Julian Rrushi’s ‘A Quest For The Physics Of Cyberspace’ appeared first on Security Boulevard.

CyberSecurity Insiders
MARCH 21, 2021
Prevalence of breach attempts can be attributed to reliance on cloud as work-from-home era continues. March 17, 2021 ? An overwhelming percentage (90%) of cyberattacks on cloud environments in the last 12 months involved compromised privileged credentials, according to new research from Centrify , a leading provider of modern privileged access management (PAM) solutions.

Security Boulevard
MARCH 21, 2021
Many thanks to USENIX Enigma 2021 for publishing these outstanding conference videos on the YouTube USENIX Channel ; don't miss this erudite 27 video information & cybersecurity event. Permalink. The post USENIX Enigma 2021 – Gianluca Stringhini’s ‘Computational Methods To Understand And Mitigate Online Aggression’ appeared first on Security Boulevard.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Security Affairs
MARCH 21, 2021
US CISA has released a new tool that allows detecting malicious activity associated with the SolarWinds hackers in compromised on-premises enterprise environments.

Security Boulevard
MARCH 21, 2021
Many thanks to USENIX Enigma 2021 for publishing these outstanding conference videos on the YouTube USENIX Channel ; don't miss this erudite 27 video information & cybersecurity event. Permalink. The post USENIX Enigma 2021 – Marcus Botacin’s ‘Does Your Threat Model Consider Country And Culture? A Case Study Of Brazilian Internet Banking Security To Show That It Should!
Let's personalize your content