Long Story on the Accused CIA Vault 7 Leaker
Schneier on Security
JUNE 6, 2022
Long article about Joshua Schulte, the accused leaker of the WikiLeaks Vault 7 and Vault 8 CIA data. Well worth reading.

Schneier on Security
JUNE 6, 2022
Long article about Joshua Schulte, the accused leaker of the WikiLeaks Vault 7 and Vault 8 CIA data. Well worth reading.

The Last Watchdog
JUNE 6, 2022
Reducing the attack surface of a company’s network should, by now, be a top priority for all organizations. Related: Why security teams ought to embrace complexity. As RSA Conference 2022 gets underway today in San Francisco, advanced systems to help companies comprehensively inventory their cyber assets for enhanced visibility to improve asset and cloud configurations and close security gaps will be in the spotlight.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
JUNE 6, 2022
The internet-facing instances are currently being accessed by attackers who remove the vulnerable databases and leave a ransom note instead. The post Thousands of unprotected Elasticsearch databases are being ransomed appeared first on TechRepublic.

Cisco Security
JUNE 6, 2022
Eighty-one percent of organizations told Gartner they have a multi-cloud strategy. As more organizations subscribe to cloud offerings for everything from hosted data centers to enterprise applications, the topology of the typical IT environment grows increasingly complex. Now add the proliferation of hybrid work environments , the rapid ascendance of Internet of Things (IoT) devices, and an increasingly sophisticated and malicious cyber threat landscape, and it becomes immediately clear that pro

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.
Tech Republic Security
JUNE 6, 2022
Learn about the new features available with iOS 16, and how to download and install the latest version of Apple’s mobile operating system. The post iOS 16 cheat sheet: Complete guide for 2022 appeared first on TechRepublic.

SecureList
JUNE 6, 2022
At the end of May, researchers from the nao_sec team reported a new zero-day vulnerability in Microsoft Support Diagnostic Tool (MSDT) that can be exploited using Microsoft Office documents. It allowed attackers to remotely execute code on Windows systems, while the victim could not even open the document containing the exploit, or open it in Protected Mode.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
Security Affairs
JUNE 6, 2022
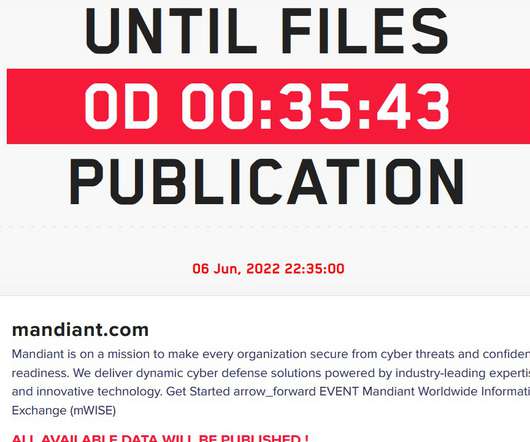
LockBit ransomware gang claims to have hacked the cybersecurity firm Mandiant, which is investigating the alleged security breach. Today the LockBit ransomware gang has added the cybersecurity firm Mandiant to the list of victims published on its darkweb leak site. Mandiant is investigating the claims of the ransomware gang, the cybercrime group declared to have stolen 356841 files from the company and plans to leak them online.

Tech Republic Security
JUNE 6, 2022
WordPress has many managed hosting plans to choose from to help handle larger websites with higher traffic flows. Determine whether Kinsta or WP Engine is the best option for your business. The post Kinsta vs WP Engine: Managed WordPress hosting comparison appeared first on TechRepublic.

Security Affairs
JUNE 6, 2022
Resecurity, Inc. (USA) has identified an increase in activity within hacktivist groups conducted by a new group called “Cyber Spetsnaz”. Resecurity, Inc. (USA) has identified an increase in activity within hacktivist groups, they’re leveraging current geopolitical tensions between the Ukraine and Russia to perform cyber-attacks. Following the attacks of the Killnet Collective, the group responsible for the attacks against major government resources and law enforcement, a new group has been ident
Tech Republic Security
JUNE 6, 2022
Passkeys use cryptographic techniques and biometrics and aim to replace passwords for good. The post Apple touts Passkey, its new privacy feature, at WWDC 2022 appeared first on TechRepublic.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

The Hacker News
JUNE 6, 2022
Cybersecurity researchers have disclosed two unpatched security vulnerabilities in the open-source U-Boot boot loader. The issues, which were uncovered in the IP defragmentation algorithm implemented in U-Boot by NCC Group, could be abused to achieve arbitrary out-of-bounds write and denial-of-service (DoS).
Tech Republic Security
JUNE 6, 2022
With this multifunctional iOS unlocking tool, you can solve various possible problems with your iPhone, iPad or iPod touch. Get a lifetime subscription of the tool for a limited time. The post How to always access your locked iOS device appeared first on TechRepublic.

CSO Magazine
JUNE 6, 2022
Every year, global security vendors use the RSA Conference (RSAC) to exhibit new products and capabilities. This year, the show returns as an in-person event (with a virtual component) in San Francisco after going all-virtual in 2021 due to the pandemic. At RSAC 2022, starting June 6, new product showcases are dominated by identity and access security, SaaS services and security operations center ( SOC ) enhancements.
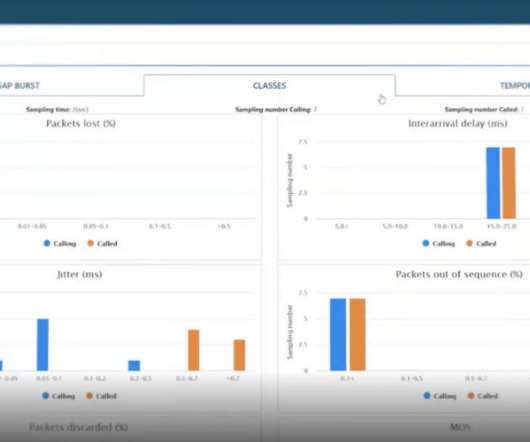
Security Affairs
JUNE 6, 2022
During the bug hunting activity, Red Team Research (RTR) detected 2 zero-day bugs on GEMINI-NET, a RESI Informatica solution. It’s been detected an OS Command Injection, which has been identified from NIST as a Critical one, its score is 9,8. This vulnerability comes from a failure to check the parameters sent as inputs into the system before they are processed by the server. .

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Malwarebytes
JUNE 6, 2022
Last week on Malwarebytes Labs: Intuit phish says “We have put a temporary hold on your account” The Quad commits to strengthening cybersecurity in software, supply chains Double-whammy attack follows fake Covid alert with a bogus bank call Microsoft Office zero-day “Follina”—it’s not a bug, it’s a feature! (It’s a bug) Is quantum teleportation the future of secure communications?

Dark Reading
JUNE 6, 2022
A panel of CISOs at the RSA Conference outlined what a successful first 90-day plan looks like, and it boiled down to effective communication and listening.
Bleeping Computer
JUNE 6, 2022
European governments and US local governments were the targets of a phishing campaign using malicious Rich Text Format (RTF) documents designed to exploit a critical Windows zero-day vulnerability known as Follina. [.].

Malwarebytes
JUNE 6, 2022
Updating endpoints on a network can be a daunting task. Testing before rollout can take time. Delays to patches going live can cause all manner of headaches. Windows Autopatch aims to tackle some of these issues, and is now live for public preview. The release comes with a few caveats which you’ll want to keep in mind. Fixing a patchy experience.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Security Affairs
JUNE 6, 2022
Microsoft’s Digital Crimes Unit (DCU) announced the seizure of domains used by Iran-linked APT Bohrium in spear-phishing campaigns. Microsoft’s Digital Crimes Unit (DCU) announced to have taken legal action to disrupt a spear-phishing operation linked to Iran-linked APT Bohrium. The IT giant has seized the domains used by the threat actors employed in its attacks aimed at organizations in tech, transportation, government, and education sectors located in the U.S., Middle East, and In

Security Boulevard
JUNE 6, 2022
A nasty zero-click, zero-day RCE bug remains unpatched in Windows. Dubbed “Follina,” Microsoft’s done diddly-squat about it. The post Broken Windows: ‘Follina’ Flaw not Fixed — For 22 MONTHS appeared first on Security Boulevard.

Heimadal Security
JUNE 6, 2022
Phishing is a deceptive tactic used to obtain sensitive user information (credit card numbers, passwords, etc.). Attackers appear to be trustworthy organizations (typically mimicking a large brand) to deceive victims into disclosing private data. If phishing is effective, hostile third parties steal confidential data. Financial or identity theft is committed using stolen information.

The Hacker News
JUNE 6, 2022
10 of the most prolific mobile banking trojans have set their eyes on 639 financial applications that are available on the Google Play Store and have been cumulatively downloaded over 1.01 billion times. Some of the most targeted apps include Walmart-backed PhonePe, Binance, Cash App, Garanti BBVA Mobile, La Banque Postale, Ma Banque, Caf - Mon Compte, Postepay, and BBVA México.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

The State of Security
JUNE 6, 2022
Apple says that it protected many millions of users from being defrauded to the tune of nearly $1.5 billion dollars in the last year, by policing its official App Store. According to a newly published report by Apple, over 1.6 million risky and untrustworthy apps and app updates were stopped in their tracks due to […]… Read More. The post Apple protected App Store users from $1.5 billion fraud last year appeared first on The State of Security.

CyberSecurity Insiders
JUNE 6, 2022
Hackers were seen using Jersey computers to cyber attack servers operating in the United States, Germany and Hungary. The compromised machines were acting as devices to launch cyber attacks and the suspicion finger is currently rising towards Russia. The Cyber Emergency Response Team (CERT) of the UK based island has confirmed the news and stated that the criminals behind the digital assaults will be made public as soon as the investigation completes.
Security Affairs
JUNE 6, 2022
A nation-state actor is attempting to exploit the Follina flaw in a recent wave of attacks against government entities in Europe and the U.S. An alleged nation-state actor is attempting to exploit the recently disclosed Microsoft Office Follina vulnerability in attacks aimed at government entities in Europe and the U.S. On May 31, Microsoft released workarounds for a recently discovered zero-day vulnerability, dubbed Follina and tracked as CVE-2022-30190 (CVSS score 7.8), in the Microsoft Office

Heimadal Security
JUNE 6, 2022
ACY Securities is an Australian financial derivative trading organization that allows customers to trade Forex (FX) and CFD instruments across shares, indices, precious metals, commodities, and cryptocurrencies. According to Anurag Sen, a well-known cybersecurity researcher, the Australia-based trading company unintentionally revealed a large amount of personal and financial information belonging to unsuspecting users and organizations […].

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Bleeping Computer
JUNE 6, 2022
The municipality of Palermo in Southern Italy suffered a cyberattack on Friday, which appears to have had a massive impact on a broad range of operations and services to both citizens and visiting tourists. [.].

Malwarebytes
JUNE 6, 2022
Prometheus—a ransomware build based on Thanos that locked up victims’ computers in the summer of 2021—included a major “vulnerability” that led security researchers at IBM to try and build a one-size-fits-all ransomware decryptor that could work against multiple ransomware variants, including Prometheus, AtomSilo, LockFile, Bandana, Chaos, and PartyTicket.

The Hacker News
JUNE 6, 2022
Microsoft's Digital Crimes Unit (DCU) last week disclosed that it had taken legal proceedings against an Iranian threat actor dubbed Bohrium in connection with a spear-phishing operation. The adversarial collective is said to have targeted entities in tech, transportation, government, and education sectors located in the U.S., Middle East, and India.
Security Boulevard
JUNE 6, 2022
We have covered everything you need to know about defence-in-depth strategy including its definition, importance and relation to layered security. The post Defense in Depth – Definition & Relation to Layered Security Approach appeared first on Cyphere | Securing Your Cyber Sphere. The post Defense in Depth – Definition & Relation to Layered Security Approach appeared first on Security Boulevard.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content