New SEC Rules around Cybersecurity Incident Disclosures
Schneier on Security
AUGUST 2, 2023
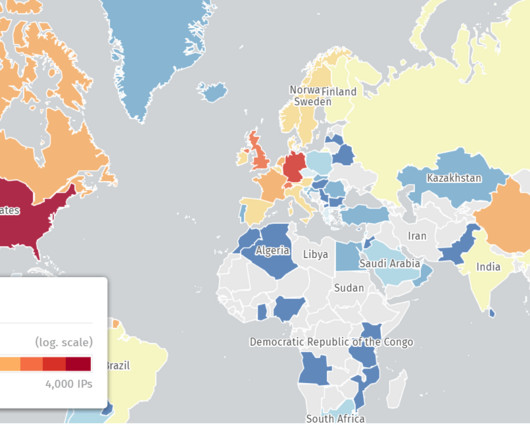
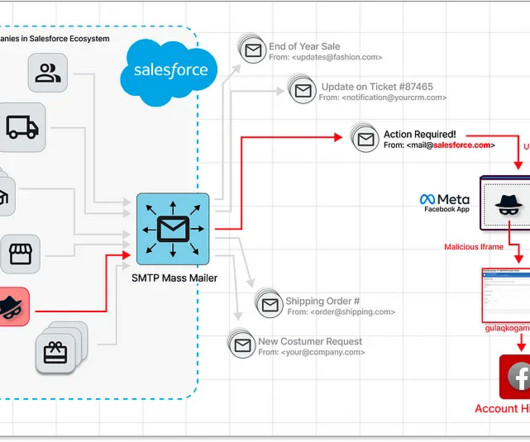
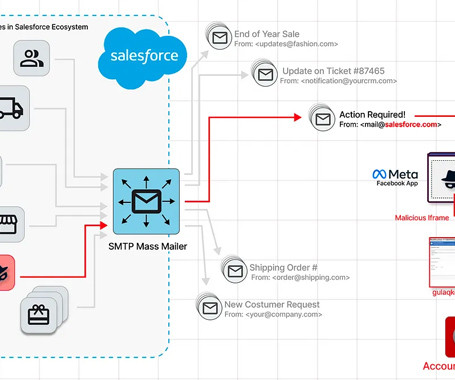
The US Securities and Exchange Commission adopted final rules around the disclosure of cybersecurity incidents. There are two basic rules: Public companies must “disclose any cybersecurity incident they determine to be material” within four days, with potential delays if there is a national security risk. Public companies must “describe their processes, if any, for assessing, identifying, and managing material risks from cybersecurity threats” in their annual filings.


































Let's personalize your content