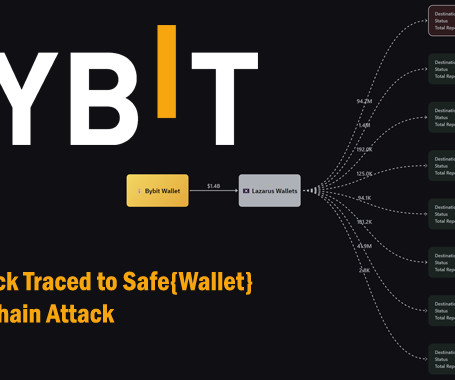
Bybit Hack: $1.46 Billion Crypto Heist Points to North Korea's Lazarus Group
SecureWorld News
FEBRUARY 26, 2025
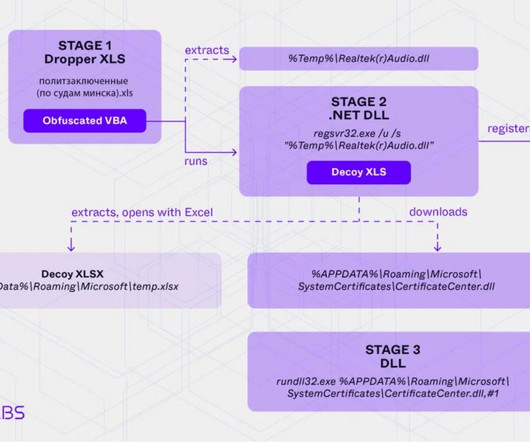
On February 21, 2025, the cryptocurrency world was rocked by the largest crypto heist in history. Dubai-based exchange Bybit was targeted in a malware-driven attack that resulted in the theft of approximately $1.46 billion in crypto assets. With investigators rapidly tracing the digital breadcrumbs, several experts have now pointed to North Korea's notorious Lazarus Group as the likely culprit behind the audacious breach.







































Let's personalize your content