LastPass Security Breach
Schneier on Security
DECEMBER 2, 2022
The company was hacked , and customer information accessed. No passwords were compromised.

Schneier on Security
DECEMBER 2, 2022
The company was hacked , and customer information accessed. No passwords were compromised.

Joseph Steinberg
DECEMBER 2, 2022
I am happy (and proud) to announce that SecureMySocial, a cybersecurity company that I co-founded, has been issued its fifth United States patent for social media security. The patent was issued by the United States Patent Office on September 6th, 2022, with a priority date going back over a decade, to June of 2012. Patent number US 11,438,334 entitled Systems and Methods for Securing Social Media for Users and Businesses and Rewarding for Enhancing Security , discloses a robust invention that a
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
DECEMBER 2, 2022
Qualys researchers demonstrated how to chain a new Linux flaw with two other two issues to gain full root privileges on an impacted system. Researchers at the Qualys’ Threat Research Unit demonstrated how to chain a new Linux vulnerability, tracked as CVE-2022-3328 , with two other flaws to gain full root privileges on an affected system. The vulnerability resides in the snap-confine function on Linux operating systems, a SUID-root program installed by default on Ubuntu.
Graham Cluley
DECEMBER 2, 2022
Researchers investigating a newly-discovered botnet have admitted that they "accidentally" broke. Read more in my article on the Tripwire State of Security blog.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Security Affairs
DECEMBER 2, 2022
Experts found multiple flaws in three Android Keyboard apps that can be exploited by remote attackers to compromise a mobile phone. Researchers at the Synopsys Cybersecurity Research Center (CyRC) warn of three Android keyboard apps with cumulatively two million installs that are affected by multiple flaws ( CVE-2022-45477, CVE-2022-45478, CVE-2022-45479, CVE-2022-45480, CVE-2022-45481, CVE-2022-45482, CVE-2022-45483 ) that can be exploited by attackers to compromise a mobile phone.
Naked Security
DECEMBER 2, 2022
We grabbed the update, based on no information at all, just in case we came across a reason to advise you not to. So far, so good.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
DECEMBER 2, 2022
Google has released Chrome 108.0.5359.94/.95 for Windows, Mac, and Linux users to address a single high-severity security flaw, the ninth Chrome zero-day exploited in the wild patched since the start of the year. [.].

InfoWorld on Security
DECEMBER 2, 2022
There seems to be a clear trend in the world of cloud computing to return to IT fundamentals—the core problems that IT was set up to solve, such as data management, security, operations, governance, and development. All these things have been practiced for many decades and should be practiced now. The issue is not that IT is ignoring the fundamentals as they build and deploy major business systems in the cloud.

SecureList
DECEMBER 2, 2022
It would hardly be an exaggeration to say that the phrase “indicators of compromise” (or IOCs) can be found in every report published on the Securelist. Usually after the phrase there are MD5 hashes [1] , IP addresses and other technical data that should help information security specialists to counter a specific threat. But how exactly can indicators of compromise help them in their everyday work?

InfoWorld on Security
DECEMBER 2, 2022
Software runs our businesses today. It powers operations, transactions, communications—just about every facet of the digital organization. It follows that ensuring the security of applications and operating systems is a major priority for development and security teams. This is where DevSecOps plays a key role. Development, security, and operations.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

The Hacker News
DECEMBER 2, 2022
The new Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA) requires CISA to create rules regarding cyber incident reporting by critical infrastructure organizations. The RFI and hearings precede a Notice of Proposed Rulemaking (NPRM) that CISA must publish sooner than 24 months from the enactment of CIRCIA, which the President signed into law in March.

Security Boulevard
DECEMBER 2, 2022
Eufy home security cameras and doorbells are insecure: They send your photos to the cloud without permission and serve up video across the internet without encryption. The post More Lies: Anker’s Eufy Pants on Fire — ‘No Cloud’ Cams Send to Cloud appeared first on Security Boulevard.

The Hacker News
DECEMBER 2, 2022
Platform certificates used by Android smartphone vendors like Samsung, LG, and MediaTek have been found to be abused to sign malicious apps. The findings were first discovered and reported by Google reverse engineer ?ukasz Siewierski on Thursday.

Security Boulevard
DECEMBER 2, 2022
The Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory calling for increased consumer vigilance as malicious actors attempt to take advantage of unsuspecting holiday shoppers through malicious links, fake websites and other forms of cybercrime. The CISA outlined a handful of preventative actions for consumers, including checking personal devices, shopping from trusted sources, using.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

CyberSecurity Insiders
DECEMBER 2, 2022
New malware is on the prowl and is seen spreading malicious software in disguise of applications meant for teaching, reading, and other education-related activities. In particular, the apps targeted users from Vietnam and infected about 300,000 devices in over 71 countries just to steal Facebook(FB) credentials. ZIMPERIUM is the firm that conducted the study and discovered the infection in the wild in 2018.
Security Boulevard
DECEMBER 2, 2022
Software composition analysis is an essential part of application security. Here are the important factors to consider when selecting an SCA scanner to be sure it is well-suited to your needs. The post 9 Things to Consider When Choosing an SCA Tool appeared first on Security Boulevard.

eSecurity Planet
DECEMBER 2, 2022
A user calls into the helpdesk reporting that their system is down. Upon investigation, you discover it’s ransomware. Servers are encrypted with “ locked” file extensions on files. Ransom notes are on the desktops. No problem, just restore, right? You have the disaster recovery (DR) site, backups, and storage area network (SAN) snapshots.
Security Boulevard
DECEMBER 2, 2022
Australia’s cybersecurity, government, and critical infrastructure communities are joining forces in a collaborative effort to uplift the nation’s human-cyber resilience. Last week DTEX Systems joined the Australian Cyber Collaboration Centre, MITRE Corporation, Providence Consulting Group, and other industry and government delegates in Melbourne for a discussion on Australia’s Security of Critical Infrastructure (SOCI) Act reforms. … Continued.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

CSO Magazine
DECEMBER 2, 2022
Using multi-factor authentication (MFA) is one of the key components of an organizations Identity and Access Management (IAM) program to maintain a strong cybersecurity posture. Having multiple layers to verify users is important, but MFA fatigue is also real and can be exploited by hackers. Enabling MFA for all accounts is a best practice for all organizations, but the specifics of how it is implemented are significant because attackers are developing workarounds.
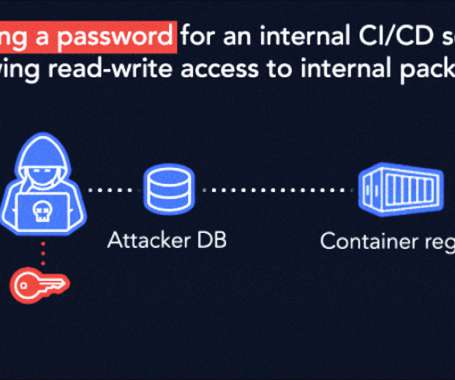
The Hacker News
DECEMBER 2, 2022
IBM has fixed a high-severity security vulnerability affecting its Cloud Databases (ICD) for PostgreSQL product that could be potentially exploited to tamper with internal repositories and run unauthorized code. The privilege escalation flaw (CVSS score: 8.

Bleeping Computer
DECEMBER 2, 2022
The Spanish National Police have arrested 55 members of the 'Black Panthers' cybercrime group, including one of the organization's leaders based in Barcelona. [.].

WIRED Threat Level
DECEMBER 2, 2022
Device manufacturers use “platform certificates” to verify an app’s authenticity, making them particularly dangerous in the wrong hands.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

SecureBlitz
DECEMBER 2, 2022
This post will show you 6 ways to protect your business from phishing attacks… Phishing attacks, if successful, can be quite harmful to your business. Statistics indicate that over 70% of phishing emails are opened, and 90% of security breaches in organizations are due to phishing attacks. As a result, small and medium-sized businesses averagely […].

We Live Security
DECEMBER 2, 2022
Deployed against carefully selected targets, the new backdoor combs through the drives of compromised systems for files of interest before exfiltrating them to Google Drive. The post ScarCruft updates its toolset – Week in security with Tony Anscombe appeared first on WeLiveSecurity.

IT Security Guru
DECEMBER 2, 2022
That CTOs should be concerned about cybersecurity and data breaches is perhaps not the biggest surprise. 2022 has seen more data breaches than ever before, and it feels like the impact of a breach is increasing too. Damage to the brand, paying ransomware costs, time and resources to address the breach, data privacy law penalties – these are all implications that contribute to cybersecurity fears being cited as the main thing keeping CTOs awake at night, according to our recent research, the Stat

Bleeping Computer
DECEMBER 2, 2022
This week's big news was the Colombia health system being severely disrupted by a ransomware attack on Keralty, one of the country's largest healthcare providers. [.].

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Dark Reading
DECEMBER 2, 2022
A do-it-yourself machine-learning system helped a French bank detect three types of exfiltration attacks missed by current rules-based systems, attendees will learn at Black Hat Europe.

Security Affairs
DECEMBER 2, 2022
Cuba ransomware gang received more than $60 million in ransom payments related to attacks against 100 entities worldwide as of August 2022. The threat actors behind the Cuba ransomware (aka COLDDRAW, Tropical Scorpius ) have demanded over 145 million U.S. Dollars (USD) and received more than $60 million in ransom payments from over 100 victims worldwide as of August 2022, the US government states.

Bleeping Computer
DECEMBER 2, 2022
A new residential proxy market is becoming popular among hackers, cybercriminals, phishers, scalpers, and scammers, selling access to a million claimed proxy IP addresses worldwide. [.].

The Hacker News
DECEMBER 2, 2022
Search giant Google on Friday released an out-of-band security update to fix a new actively exploited zero-day flaw in its Chrome web browser. The high-severity flaw, tracked as CVE-2022-4262, concerns a type confusion bug in the V8 JavaScript engine. Clement Lecigne of Google's Threat Analysis Group (TAG) has been credited with reporting the issue on November 29, 2022.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content