Deepfake Election Interference in Slovakia
Schneier on Security
OCTOBER 6, 2023
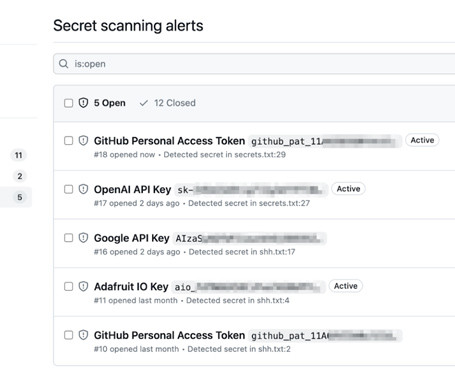
Well designed and well timed deepfake or two Slovakian politicians discussing how to rig the election: Šimečka and Denník N immediately denounced the audio as fake. The fact-checking department of news agency AFP said the audio showed signs of being manipulated using AI. But the recording was posted during a 48-hour moratorium ahead of the polls opening, during which media outlets and politicians are supposed to stay silent.






































Let's personalize your content