Remote Work Nearly Killed Email Etiquette. Let’s Bring It Back
Lohrman on Security
AUGUST 15, 2021
Email tips abound, but lasting email etiquette is severely lacking at home and work in 2021.

Lohrman on Security
AUGUST 15, 2021
Email tips abound, but lasting email etiquette is severely lacking at home and work in 2021.

Trend Micro
AUGUST 15, 2021
The ransomware group LockBit resurfaced in July with LockBit 2.0, with reports indicating an increased number of targeted companies and the incorporation of double extortion features. Our detections followed attack attempts in Chile, Italy, Taiwan, and the UK from July to August.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Bleeping Computer
AUGUST 15, 2021
A threat actor claims to have hacked T-Mobile's servers and stolen databases containing the personal data of approximately 100 million customers. [.].

CyberSecurity Insiders
AUGUST 15, 2021
T-Mobile that occupies over 35% of mobile subscriber base in United States has launched a detailed probe after receiving several media concerns that over 100 million T mobile customer data was available on sale on the dark web. Cybersecurity Insiders has learnt that a hackers group has published the stolen data on a hacking forum that includes information related to T-Mobile customers like social security number, phone numbers, names, physical addresses, and driving licenses.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Bleeping Computer
AUGUST 15, 2021
A bug on Ford's website allowed for accessing sensitive systems and obtaining proprietary data, such as customer databases, employee records, internal tickets, etc. The data exposure stemmed from a misconfigured instance of Pega customer engagement system running on Ford's servers. [.].

CyberSecurity Insiders
AUGUST 15, 2021
Car makers Toyota, Hyundai and Nissan are all set to form a consortium that will aim to fight cyber attacks on Connected Cars. And companies like Microsoft Japan, Trend Micro, NTT Communications, Sompo Japan Insurance and few other manufacturers like Panasonic and Denso are all set to join the campaign. According to an Asian news resource, Nikkei Asia, the aim of the consortium will be to prevent hackers from hijacking autonomous vehicles and preventing theft of data.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
AUGUST 15, 2021
If you can't find your favorite Windows Subsystem for Linux distribution available in the Microsoft Store, a new program called EasyWSL can convert almost any Linux Docker image into a WSL distro. [.].
Elie
AUGUST 15, 2021
This keynote discusses whether applying deep-learning to cryptanalysis will revolutionize the field or if it will go out of fashion in a few years due to the lack of breakthroughs.

Security Boulevard
AUGUST 15, 2021
Welcome to the Ask Chloé column on Security Boulevard! Each week, Chloé provides answers to readers’ questions to help guide them as they navigate the technology industry. This week, Chloé helps a cybersecurity pro to better organize their time and become more productive. Dear Chloé, I’ve been trying to become more organized and feeling. The post Ask Chloé: Improving Productivity as an InfoSec IC appeared first on Security Boulevard.

Security Affairs
AUGUST 15, 2021
T-Mobile is investigating a possible data breach after a threat actor published a post on a forum claiming to be selling the personal data of its customers. New problems for T-Mobile, the company is investigating a possible data breach after that a threat actor has published a post on a hacking forum claiming to be in possession of the personal data of its customers.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Security Boulevard
AUGUST 15, 2021
Over $600 million stolen in the largest DeFi cryptocurrency hack in history, attackers are getting around $10k for stolen network access credentials, and why your identity is trapped inside a social network and what this means for the next potential evolution of the Internet…the metaverse! ** Links mentioned on the show ** Apple to refuse […]. The post Largest Cryptocurrency Hack in History, $10k For Stolen Network Access, Your Identity and the Metaverse appeared first on The Shared Security Sho

Security Affairs
AUGUST 15, 2021
A job ad published by the UK’s Ministry of Defence has revealed the existence of a previously undisclosed secret SAS mobile hacker team. The existence of a secret SAS mobile hacker squad, named MAB5 and under the control of the Computer Network Operations (CNO) Exploitation, was revealed by a job ad published by the UK’s Ministry of Defence on an external website, reported Alan Turnbull of Secret Bases.

Security Boulevard
AUGUST 15, 2021
Today’s enterprise operations involve the coordination of several different digital ecosystems but none quite so inflamed as the cybersecurity ecosystem. Technology has been evolving at a rapid pace, and attackers are armed with advanced tactics to steal data and expose secure information. In response, cybersecurity teams deploy numerous tools and solutions to prevent and mitigate […]… Read More.

WIRED Threat Level
AUGUST 15, 2021
Need to be discreet? Here's how to set up vanishing texts, photos, or videos in most popular chat apps.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
AUGUST 15, 2021
via the comic artistry and dry wit of Randall Munroe , resident at XKCD ! Permalink. The post XKCD ‘Every Data Table’ appeared first on Security Boulevard.

Mitnick Security
AUGUST 15, 2021
So, you've decided to run a penetration test against your organization. But now. what do you do with the results? With so many vulnerabilities exposed, where should you even start? As a matter of fact, how do you even read this technical report?
Security Boulevard
AUGUST 15, 2021
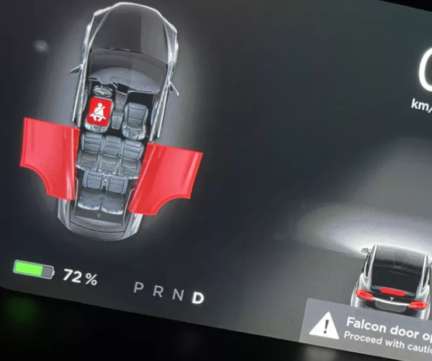
A video making the rounds on social media asks the simple question how a Tesla driver can ignore big red warning lights and “proceed with caution” text on the dashboard? Perhaps the better question is why engineers fail to close the door as its wheels start moving (obviously with obstruction sensors to prevent crushing things, … Continue reading Tesla Ajar “Falcon” Door Hits London Bus ?.

Thales Cloud Protection & Licensing
AUGUST 15, 2021
What if Identity Security and Access Management Didn’t Exist? sparsh. Mon, 08/16/2021 - 06:56. Authored by Karen Kelvie, Partner Marketing at Thales, and Taylor Wiggins, Product Marketing Manager - Technology Alliance at SailPoint. In the world of tech, we love to future gaze. But while imagining potential new developments is exciting, it can be equally helpful to think about the reverse: How would things be different if certain technologies didn’t exist?

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Boulevard
AUGUST 15, 2021
The COVID-19 scare has more people than ever are working at home. While this isn’t a new trend, it is affecting people on a much more massive scale now in light of the current health frenzy. The giants have taken heed: Amazon, Facebook, Google, Microsoft among others have all disseminated their office workers in specific […]. The post The Coronavirus Cyber Doc Diagnosis: Work from Home appeared first on HolistiCyber.

Security Affairs
AUGUST 15, 2021
A new round of the weekly Security Affairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the international press subscribe here. Four years after its takedown, AlphaBay marketplace revamped Classified documents from Lithuanian Ministry of Foreign Affairs are available for sale Dumping user’s Microsoft Azure credentials in plaintext from Windows 365 SynAck ransomware gang releases master decryp

Security Boulevard
AUGUST 15, 2021
A very good summary of the COVID-19 Vaccine has this paragraph buried in the seventh section, under “preventing disease and death”. The vaccine shows an 8-fold reduction in the development of any symptomatic disease secondary to delta. For hospitalization, it is a 25-fold reduction. That’s 25 times! Remarkable. For death, it is also 25 times! … Continue reading COVID-19 vaccines rated “best overall pharmaceuticals on the market in any class” ?.

Security Boulevard
AUGUST 15, 2021
Our thanks to DEFCON for publishing their outstanding DEFCON Conference Main Stage Videos on the groups' YouTube channel. Permalink. The post DEF CON 29 Main Stage – Reza Soosahabi’s & Chuck McAuley’s – SPARROW: A Novel Covert Communication Scheme appeared first on Security Boulevard.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Security Boulevard
AUGUST 15, 2021
Our thanks to DEFCON for publishing their outstanding DEFCON Conference Main Stage Videos on the groups' YouTube channel. Permalink. The post DEF CON 29 Main Stage – Richard Henderson’s ‘Old MacDonald Had A Barcode, E I E I CAR’ appeared first on Security Boulevard.
Let's personalize your content