Defeating Phishing-Resistant Multifactor Authentication
Schneier on Security
NOVEMBER 9, 2022
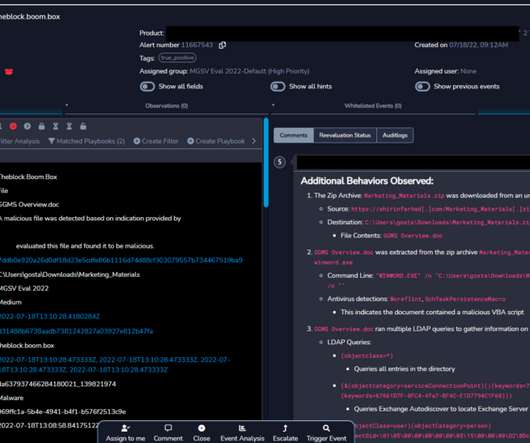
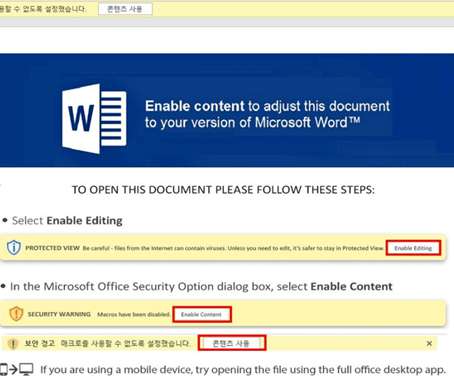
CISA is now pushing phishing-resistant multifactor authentication. Roger Grimes has an excellent post reminding everyone that “phishing-resistant” is not “phishing proof,” and that everyone needs to stop pretending otherwise. His list of different attacks is particularly useful.









































Let's personalize your content