68k Phishing Victims are Now Searchable in Have I Been Pwned, Courtesy of CERT Poland
Troy Hunt
AUGUST 30, 2023
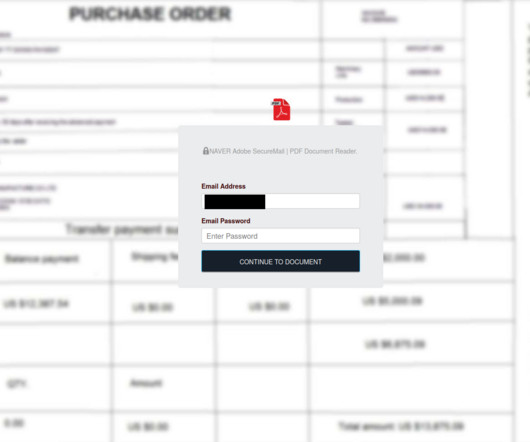
Last week I was contacted by CERT Poland. They'd observed a phishing campaign that had collected 68k credentials from unsuspecting victims and asked if HIBP may be used to help alert these individuals to their exposure. The campaign began with a typical email requesting more information: In this case, the email contained a fake purchase order attachment which requested login credentials that were then posted back to infrastructure controlled by the attacker: All in all, CERT Poland identifi



































Let's personalize your content