Google Stops Collecting Location Data from Maps
Schneier on Security
DECEMBER 26, 2023
Google Maps now stores location data locally on your device, meaning that Google no longer has that data to turn over to the police.

Schneier on Security
DECEMBER 26, 2023
Google Maps now stores location data locally on your device, meaning that Google no longer has that data to turn over to the police.

Bleeping Computer
DECEMBER 26, 2023
GitHub is warning users that they will soon have limited functionality on the site if they do not enable two-factor authentication (2FA) on their accounts. [.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Malwarebytes
DECEMBER 26, 2023
Phishing is the art of sending an email with the aim of getting users to open a malicious file or click on a link to then steal credentials. But most phishers aren’t very good, and the success rate is relatively low: In 2021, the average click rate for a phishing campaign was 17.8%. However, now cybercriminals have AI to write their emails, which might well improve their phishing success rates.

Security Affairs
DECEMBER 26, 2023
Cybersecurity company Resecurity has published the 2024 Cyber Threat Landscape Forecast. Resecurity, a Los Angeles-based cybersecurity company protecting Fortune 100 and government agencies worldwide, has compiled a comprehensive forecast outlining the imminent threats and novel security challenges anticipated in the upcoming year. These projections stem from an in-depth analysis of the underground economy’s evolution on the Dark Web and a thorough examination of significant cybersecurity

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Bleeping Computer
DECEMBER 26, 2023
Integris Health patients in Oklahoma are receiving blackmail emails stating that their data was stolen in a cyberattack on the healthcare network, and if they did not pay an extortion demand, the data would be sold to other threat actors. [.
Security Affairs
DECEMBER 26, 2023
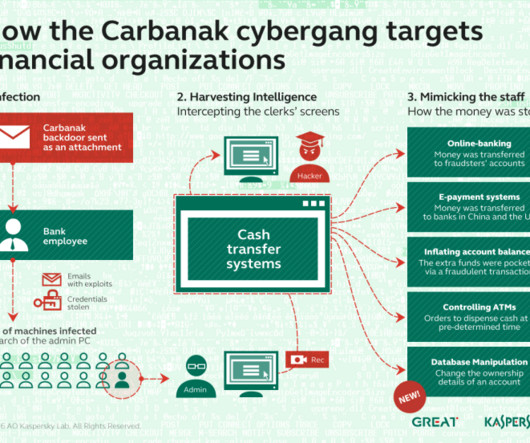
Researchers at NCC Group reported that in November they observed the return of the infamous banking malware Carbanak in ransomware attacks. The cybersecurity firm NCC Group reported that in November the banking malware Carbanak was observed in ransomware attacks. The Carbanak gang was first discovered by Kaspersky Lab in 2015, the group has stolen at least $300 million from 100 financial institutions.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Penetration Testing
DECEMBER 26, 2023
403-bypass Are you interested in web security and want to test your skills against potential 403 bypasses? If so, you’ve come to the right place! This project is a comprehensive suite of Bash scripts,... The post 403-bypass: comprehensive suite of Bash scripts for probing 403 bypasses in web security appeared first on Penetration Testing.

The Hacker News
DECEMBER 26, 2023
Poorly secured Linux SSH servers are being targeted by bad actors to install port scanners and dictionary attack tools with the goal of targeting other vulnerable servers and co-opting them into a network to carry out cryptocurrency mining and distributed denial-of-service (DDoS) attacks.

Penetration Testing
DECEMBER 26, 2023
In the vast expanse of the digital ocean, a new wave of cyber attacks has emerged, targeting the seemingly unassuming Linux SSH servers. These attacks, meticulously analyzed by the experts at AhnLab Security Emergency... The post Open Door Under Linux: Hackers Surf a Wave of Server Breaches appeared first on Penetration Testing.
Hack the Box
DECEMBER 26, 2023
An in-depth look at CVE-2022-0492: a container escape vulnerability that does not require a specific authorization capability to be granted to be exploited.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

SecureBlitz
DECEMBER 26, 2023
This post will show you the easy steps to port your mobile number to a different operator. In the dynamic world of mobile telecommunications, the ability to switch operators while retaining your existing mobile number has become a valuable and straightforward process. If you find yourself considering a change and wondering about your Airtel port […] The post Easy Steps To Port Your Mobile Number To A Different Operator appeared first on SecureBlitz Cybersecurity.

Penetration Testing
DECEMBER 26, 2023
In the shadowy realms of cyber threats, a formidable entity known as PhantomControl has emerged, marking its presence with intricate and sophisticated cyberattacks. First observed by eSentire’s Threat Response Unit in November 2023, PhantomControl’s... The post eSentire vs. Phantom: Unveiling the Cyber Spook’s Dance of Darkness appeared first on Penetration Testing.

SecureBlitz
DECEMBER 26, 2023
In this post, I will talk about projecting future solar energy requirements. Picture this: a world where energy is abundant, clean, and accessible to everyone. A world where the power of the sun fuels our homes, businesses, and dreams. As we navigate the challenges of a changing climate, the need for sustainable energy has never […] The post Projecting Future Solar Energy Requirements: A Journey into Sustainable Power appeared first on SecureBlitz Cybersecurity.

Quick Heal Antivirus
DECEMBER 26, 2023
Beware! Behind the face of advancing technology lies a dark underbelly – that of evolving cyber crime. Here, The post Beware: Fake Apps posing as Open AI’s ChatGPT App appeared first on Quick Heal Blog.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

InfoWorld on Security
DECEMBER 26, 2023
Most security issues in the cloud can be traced back to someone doing something stupid. Sorry to be that blunt, but I don’t see ingenious hackers out there. I do see misconfigured cloud resources, such as storage and databases, that lead to vulnerabilities that could easily be avoided. I always teach how your first line of defense is not cool security tools but training.
Security Boulevard
DECEMBER 26, 2023
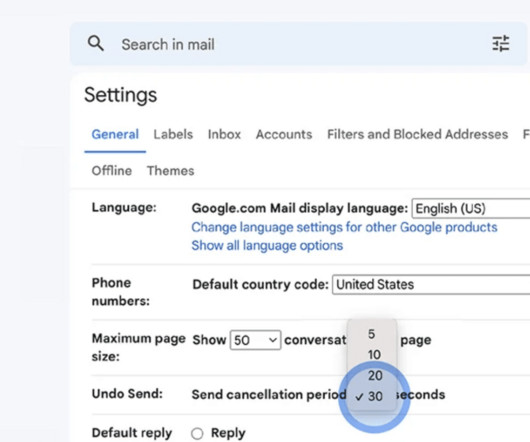
Noticed an error right after sending an email? Learn how to unsend an email in Outlook, Gmail, and Yahoo and save yourself from oops moments. The post How to Unsend an Email and Save Yourself from Oops Moments? appeared first on Security Boulevard.

Penetration Testing
DECEMBER 26, 2023
Apache OFBiz is an open-source product for the automation of enterprise processes. It includes framework components and business applications for ERP, CRM, E-Business/E-Commerce, Supply Chain Management, and Manufacturing Resource Planning. OFBiz provides a foundation... The post CVE-2023-51467: Apache OFBiz Pre-Authentication RCE Vulnerability appeared first on Penetration Testing.
Security Boulevard
DECEMBER 26, 2023
By Jim Miller We’ve updated ZKDocs with four new sections and additions to existing content. ZKDocs provides explanations, guidance, and documentation for cryptographic protocols that are otherwise sparingly discussed but are used in practice. As such, we’ve added four new sections detailing common protocols that previously lacked implementation guidance: The Inner Product Argument (IPA), which […] The post We’ve added more content to ZKDocs appeared first on Security Boulevard.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.
Security Affairs
DECEMBER 26, 2023
The Rhysida ransomware group claimed to have hacked Abdali Hospital, a multi-specialty hospital located in Jordan. Abdali Hospital is a multi-specialty hospital located in the modern development of Al-Abdali, Amman, Jordan. Abdali Hospital provides care to patients in numerous specialties. Apart from its general surgery section, it has specialists in orthopedics and rheumatology, gynecology, urology and endocrinology, neurology, nephrology, pulmonology, internal medicine, oncology, infectious d

Security Boulevard
DECEMBER 26, 2023
Unlock the latest secrets detectors, automate severity scoring, and dive into GitGuardian's unique dev & sec collaboration features! The post Wrapping up Q4 2023 : new detectors, your favorite features, and what’s coming next in GitGuardian appeared first on Security Boulevard.

InfoWorld on Security
DECEMBER 26, 2023
Software development is currently undergoing a profound transformation, marked by a quiet yet remarkable surge in advanced automation. This impending shift promises to streamline the creation and deployment of high-quality applications on an unprecedented scale. Rather than a single technology spearheading this evolution, it’s a convergence of innovations.

Security Boulevard
DECEMBER 26, 2023
Microsoft recently released patches for nearly 80 new security vulnerabilities, including two zero-day exploits, CVE-2023-23397 and CVE-2023-24880. CVE-2023-23397 is an elevation-of-privilege (EoP) vulnerability in Microsoft Outlook that could allow an attacker to obtain a victim’s password hash. The vulnerability occurs when an attacker sends a message to the victim with an extended Message Application Program […] The post Detecting CVE-2023-23397: How to Identify Exploitation of the Latest Mic

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Hackology
DECEMBER 26, 2023
After allowing password sharing for years, Netflix has recently changed its policy. The password sharing is now only allowed for a single physical household. However, we also have multiple methods to bypass Netflix household. Want to know more? Make sure to read till the end. Let’s being! Since its initial years, Netflix encouraged password sharing with your friends and family, which allowed them to generate a strong user base.

Security Boulevard
DECEMBER 26, 2023
In a groundbreaking revelation, researchers from Vrije Universiteit Amsterdam have uncovered a formidable side-channel attack known as SLAM, posing a serious threat to the security of current and future CPUs manufactured by tech giants Intel, AMD, and Arm. This sophisticated exploit capitalizes on a feature unique to Intel CPUs called Linear Address Masking (LAM), akin […] The post SLAM Attack: New Vulnerability Targets Intel, AMD, Arm CPUs appeared first on TuxCare.

Security Boulevard
DECEMBER 26, 2023
Overview Recently, NSFOCUS CERT detected that OpenSSH released a security update and fixed a command injection vulnerability caused by malicious shell characters (CVE-2023-51385), with a CVSS score of 9.8; Since there is no security filtering of username and hostname input represented by %h,%u in OpenSSH’s ProxyCommand command, command injection may occur if the username or […] The post OpenSSH Command Injection Vulnerability (CVE-2023-51385) Alert appeared first on NSFOCUS, Inc., a global netwo

Security Boulevard
DECEMBER 26, 2023
Proposed Rule published in Federal Register.60-day comment period begins The Department of Defense’s CMMC program has taken a huge leap forward with the publication of the CMMC Proposed Rule on December 26th in the Federal Register. This kicks off a 60-day comment period and we expect CMMC to be in contracts by Q3-Q4 2024. Make […] The post 7 Key Takeaways from the CMMC Proposed Rule appeared first on PreVeil.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Security Boulevard
DECEMBER 26, 2023
Ukraine’s largest telecom operator, Kyivstar, was recently shut down after falling prey to a cyberattack. The Kyivstar cyber attack left millions of Ukrainians without access to cellular or internet services. Recent reports have cited the telecom operator’s CEO, Alexander Komarov, stating that the cybersecurity incident at Kyivstar was connected to ongoing conflicts with Russia.
Security Boulevard
DECEMBER 26, 2023
via the respected Software Engineering expertise of Mikkel Noe-Nygaard and the lauded Software Engineering / Enterprise Agile Coaching work of Luxshan Ratnaravi at Comic Agilé ! Permalink The post Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnaravi – #272 — Product Ops appeared first on Security Boulevard.

Security Boulevard
DECEMBER 26, 2023
Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the organizations strong commitment to Open Access. Originating from the conference’s events situated at the Anaheim Marriott ; and via the organizations YouTube channel. Permalink The post USENIX Security ’23 – Carter Slocum, Yicheng Zhang, Nael Abu-Ghazaleh, Jiasi Chen ‘Going Through The Motions: AR/VR Keylogging From User Head Motions’ appeared first on Security Boulevard.

Security Boulevard
DECEMBER 26, 2023
Twas the day after Christmas, when all through the place, not a box was unopened, joy filled every face. The post Twas the day after Christmas, and this family was smart… appeared first on Security Boulevard.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content