The Privacy Disaster of Modern Smart Cars
Schneier on Security
NOVEMBER 10, 2023
Article based on a Mozilla report.

Schneier on Security
NOVEMBER 10, 2023
Article based on a Mozilla report.
Tech Republic Security
NOVEMBER 10, 2023
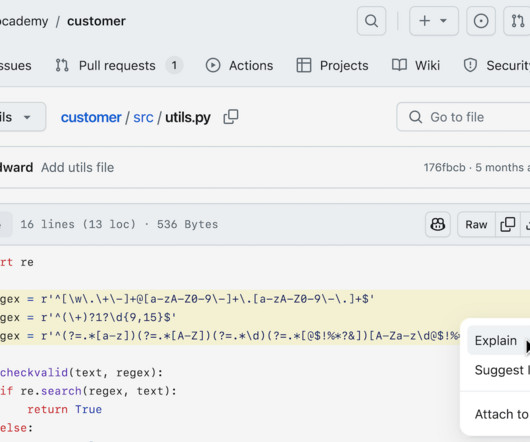
GitHub Advanced Security gains some AI features, and GitHub Copilot now includes a chatbot option. Github Copilot Enterprise is expected in February 2024.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Malwarebytes
NOVEMBER 10, 2023
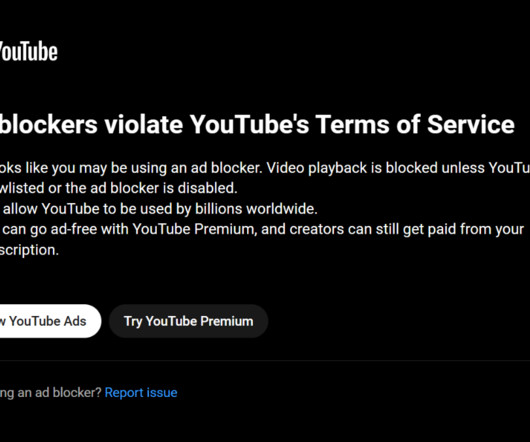
After performing local experiments for a few months, YouTube recently expanded its effort to block ad blockers. The move was immediately unpopular with some users, and raised some questions in Europe about whether it was breaking privacy laws. In addition, there are some still some fundamental issues that have some people concerned. In this blog post, we look at a couple of examples that erode our trust in online ads.

Tech Republic Security
NOVEMBER 10, 2023
Learn how to set up and use a VPN with just four easy steps. This step-by-step guide takes you through how you can secure your connection and online data.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.
Security Affairs
NOVEMBER 10, 2023
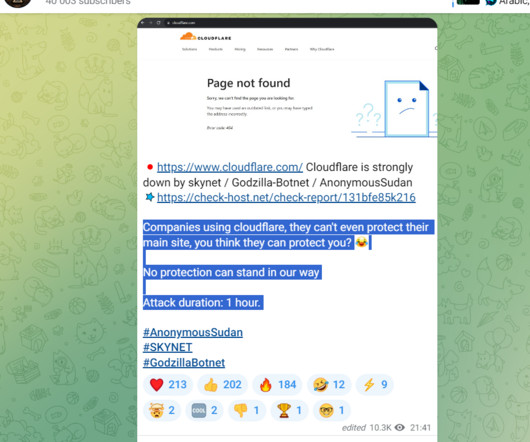
After ChatGPT, Anonymous Sudan took down the Cloudflare website with a distributed denial-of-service (DDoS) attack. The hacktivist group Anonymous Sudan claimed responsibility for the massive distributed denial-of-service (DDoS) attack that took down the website of Cloudflare. Cloudflare confirmed that a DDoS attack took down its website for a few minutes and ponited out that it did not impact other products or services. “ To be clear, there was no Cloudflare breach.

Tech Republic Security
NOVEMBER 10, 2023
SysAid has patched a zero-day vulnerability that could allow attackers to exfiltrate data and launch ransomware.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Graham Cluley
NOVEMBER 10, 2023
The US trading arm of the Industrial and Commercial Bank of China (ICBC) has been hit by a ransomware attack that reportedly forced it to handle trades via messengers carrying USB thumb drives across Manhattan. Read more in my article on the Hot for Security blog.

Security Boulevard
NOVEMBER 10, 2023
The global cybersecurity workforce gap has increased, and most cybersecurity pros said they had skills gaps in their organization. The post Cybersecurity Workforce Facing Critical Shortfall, AI Adoption Could Help appeared first on Security Boulevard.

Bleeping Computer
NOVEMBER 10, 2023
Security researchers are warning that hackers are targeting multiple healthcare organizations in the U.S. by abusing the ScreenConnect remote access tool. [.

We Live Security
NOVEMBER 10, 2023
By collecting, analyzing and contextualizing information about possible cyberthreats, including the most advanced ones, threat intelligence offers a critical method to identify, assess and mitigate cyber risk

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Tech Republic Security
NOVEMBER 10, 2023
Is a VPN worth it? Learn about the benefits of using a VPN and how to choose the right one for your business needs.

Bleeping Computer
NOVEMBER 10, 2023
The State of Maine has announced that its systems were breached after threat actors exploited a vulnerability in the MOVEit file transfer tool and accessed personal information of about 1.3 million, which is close to the state's entire population. [.

Security Boulevard
NOVEMBER 10, 2023
The outages that dogged OpenAI’s popular ChatGPT generative AI chatbot this week were caused by a distributed denial-of-service attack that has since been resolved, according to the company. The AI tech vendor reported a major outage across ChatGPT and its API Wednesday and then periodic outages on Thursday, attributing both incidents to a DDoS attack.

Dark Reading
NOVEMBER 10, 2023
A class action suit claims Intel knowingly sold billions of faulty chips for years. The outcome could help define where poor vulnerability remediation becomes outright negligence.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Bleeping Computer
NOVEMBER 10, 2023
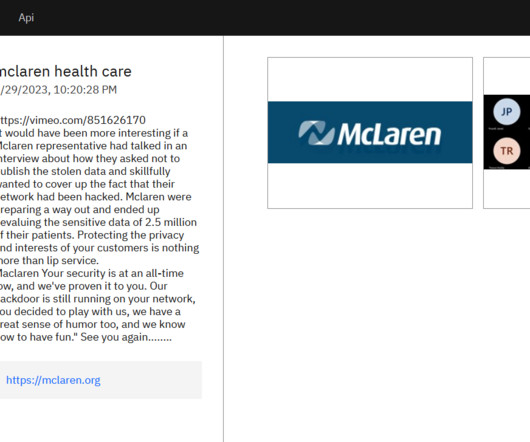
McLaren Health Care (McLaren) is notifying nearly 2.2 million people of a data breach that occurred between late July and August this year, exposing sensitive personal information. [.
Security Affairs
NOVEMBER 10, 2023
McLaren Health Care (McLaren) experienced a data breach that compromised the sensitive personal information of approximately 2.2 million individuals. McLaren Health Care (McLaren) disclosed a data breach that occurred between late July and August. The security breach exposed the sensitive personal information of 2,192,515 people. McLaren Health Care is a nonprofit health care organization based in Grand Blanc, Michigan, USA.

Bleeping Computer
NOVEMBER 10, 2023
Mr. Cooper, the largest home loan servicer in the United States, says it found evidence of customer data exposed during a cyberattack disclosed last week, on October 31. [.

Security Affairs
NOVEMBER 10, 2023
The Serbian citizen Milomir Desnica (33) has pleaded guilty to running the dark web Monopoly drug marketplace. Milomir Desnica , a 33-year-old Serbian citizen, admited to being responsible for operating the illicit Monopoly drug marketplace on the dark web. The man pleaded guilty today in U.S. District Court in the District of Columbia to charges of conspiracy to distribute and possession with intent to distribute 50 grams or more of methamphetamine.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

WIRED Threat Level
NOVEMBER 10, 2023
US government officials continue to warn that the public and private sectors need to identify and root out China-backed attackers lurking in industrial control systems.

Security Affairs
NOVEMBER 10, 2023
Microsoft spotted the exploitation of a SysAid zero-day vulnerability in limited attacks carried out by the Lace Tempest group. Microsoft reported the exploitation of a zero-day vulnerability, tracked as CVE-2023-47246 , in the SysAid IT support software in limited attacks. The IT giant linked the attacks to the Clop ransomware gang (aka Lace Tempest ).

The Hacker News
NOVEMBER 10, 2023
The notorious Russian hackers known as Sandworm targeted an electrical substation in Ukraine last year, causing a brief power outage in October 2022. The findings come from Google's Mandiant, which described the hack as a "multi-event cyber attack" leveraging a novel technique for impacting industrial control systems (ICS).

eSecurity Planet
NOVEMBER 10, 2023
DNS security protects the domain name system (DNS) from attackers seeking to reroute traffic to malicious sites. Since a majority of business IT traffic now accesses or passes through the internet, DNS plays an increasingly important — and vulnerable — role. This article will provide an overview of DNS Security, common attacks, and how to use DNS security to prevent DNS attacks and manipulation.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

The Hacker News
NOVEMBER 10, 2023
Cybersecurity researchers have discovered a stealthy backdoor named Effluence that's deployed following the successful exploitation of a recently disclosed security flaw in Atlassian Confluence Data Center and Server.
Security Affairs
NOVEMBER 10, 2023
The Industrial and Commercial Bank of China (ICBC) suffered a ransomware attack that disrupted trades in the US Treasury market. The Industrial and Commercial Bank of China (ICBC) announced it has contained a ransomware attack that disrupted the U.S. Treasury market and impacted some fixed income and equities transactions “The Securities Industry and Financial Markets Association first told members on Wednesday that ICBC Financial Services had been hit by ransomware software, which paralys

Duo's Security Blog
NOVEMBER 10, 2023
At Duo, we are committed to providing strong security and empowering users to easily access the resources they need to do their jobs. With a score of 9.3/10 and over 250 reviews, Duo is honored to share that we won the 2023 TrustRadius Top Rated Award for Authentication. Duo’s Multi-Factor Authentication solution combines multiple authentication factors to provide simple ways to protect users.

WIRED Threat Level
NOVEMBER 10, 2023
Top senate officials are planning to save the Section 702 surveillance program by attaching it to a crucial piece of legislation. Critics worry a chance to pass privacy reforms will be missed.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Dark Reading
NOVEMBER 10, 2023
ChatGPT and the associated APIs have been affected by regular outages, citing DDoS attacks as the reason — the Anonymous Sudan group claimed responsibility.

SecureList
NOVEMBER 10, 2023
Ducktail is a malware family that has been active since the second half of 2021 and aims to steal Facebook business accounts. WithSecure and GridinSoft have covered Ducktail attacks: the infostealer spread under the guise of documents relating to well-known companies’ and brands’ projects and products. Both public reports attribute the Ducktail attacks to a group that presumably hails from Vietnam.

Dark Reading
NOVEMBER 10, 2023
A 30-year-old, rarely updated protocol for medical devices has exposed reams of highly personal data, thanks to a lack of proper security throughout owner environments.

WIRED Threat Level
NOVEMBER 10, 2023
Small platforms without resources to handle takedown requests have been weaponized by terrorist groups that share their content online. A free new tool is coming to help clean house.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content