New Bluetooth Attack
Schneier on Security
DECEMBER 8, 2023
New attack breaks forward secrecy in Bluetooth. Three. news articles. The vulnerability has been around for at least a decade.

Schneier on Security
DECEMBER 8, 2023
New attack breaks forward secrecy in Bluetooth. Three. news articles. The vulnerability has been around for at least a decade.

Anton on Security
DECEMBER 8, 2023
In recent weeks, coincidentally, I’ve had several conversations that reminded me about the confusion related to “modern SOC.” Some of them were public ( example and example ), while others private. One particular person went on a quest through several “leading” companies’ security operations to see how they have implemented a “modern” SOC. However, what she found was a lot of companies improving on the classic model, with visible elements of NOC and help desk “DNA” showing (bye-bye 1990s, hi 198
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
DECEMBER 8, 2023
Connect and protect your whole team with this mini router that offers 10,000 sq ft coverage and a built-in VPN for the low price of $599.99.
Security Boulevard
DECEMBER 8, 2023
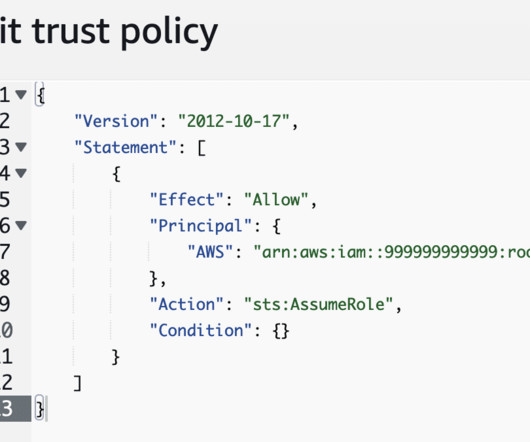
Misconfigured AWS Role Enables Cloud Initial Access The post AWS Misconfiguration Leads to Buckets of Data appeared first on Horizon3.ai. The post AWS Misconfiguration Leads to Buckets of Data appeared first on Security Boulevard.

Advertisement
Everything you need to know about better business writing in one place. This is a complete guide to business writing — from a clear business writing definition to tips on how to hone your business writing skills.
The Hacker News
DECEMBER 8, 2023
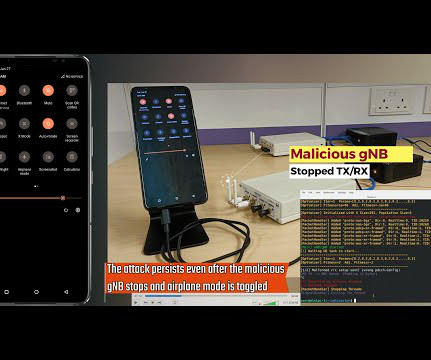
A collection of security flaws in the firmware implementation of 5G mobile network modems from major chipset vendors such as MediaTek and Qualcomm impact USB and IoT modems as well as hundreds of smartphone models running Android and iOS.
Security Affairs
DECEMBER 8, 2023
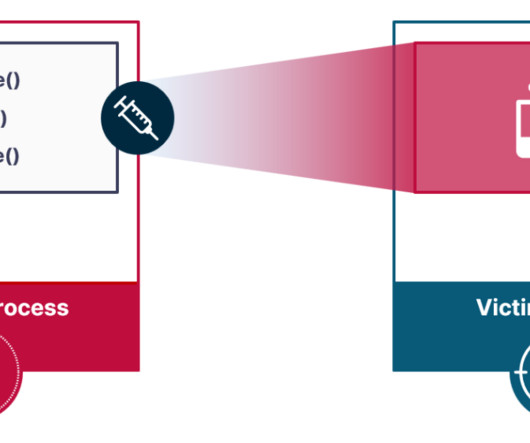
Researchers devised a novel attack vector for process injection, dubbed Pool Party, that evades EDR solutions. Researchers from cybersecurity firm SafeBreach devised a set of process injection techniques, dubbed Pool Party, that allows bypassing EDR solutions. They presented the technique at Black Hat Europe 2023. The experts relied on the less-explored Windows thread pools to discover a novel attack vector for process injection.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
DECEMBER 8, 2023
A new set of vulnerabilities in 5G modems by Qualcomm and MediaTek, collectively called "5Ghoul," impact 710 5G smartphone models from Google partners (Android) and Apple, routers, and USB modems. [.

Security Boulevard
DECEMBER 8, 2023
The introduction of generative AI has been a game changer for fraudsters, transforming ordinary schemes into highly sophisticated efforts. The post Fighting the Next Generation of Fraud appeared first on Security Boulevard.

Bleeping Computer
DECEMBER 8, 2023
Elevation of privilege flaws are the most common vulnerability leveraged by corporate insiders when conducting unauthorized activities on networks, whether for malicious purposes or by downloading risky tools in a dangerous manner. [.

Security Boulevard
DECEMBER 8, 2023
Fraud incidents are on the rise, largely attributed to the surge in impersonation fraud and the accessibility of sophisticated attack methods and tools. The post Identity Fraud Rises as E-Commerce, Payment Firms Targeted appeared first on Security Boulevard.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Bleeping Computer
DECEMBER 8, 2023
Google says it identified and fixed a bug causing customer files added to Google Drive after April-May 2023 to disappear. However, the fix isn't working for all affected users. [.

Security Boulevard
DECEMBER 8, 2023
Insight #1 Guard against island hopping. The recent ransomware attack against 60 credit unions was due to the lack of proactive cybersecurity in a managed service provider (MSP). It is high time that every organization expands penetration testing and threat hunting to their MSPs. Insight #2 As geopolitical tension manifests in cyberspace, zero days are being produced on a weekly basis.

Bleeping Computer
DECEMBER 8, 2023
Microsoft has acknowledged a new issue affecting Outlook for Microsoft 365 users and causing email-sending problems for those with too many nested folders. [.

Penetration Testing
DECEMBER 8, 2023
In the dynamic landscape of cyber threats, a new botnet, “InfectedSlurs,” has emerged, exploiting critical vulnerabilities in FXC Routers to orchestrate a sophisticated Distributed Denial of Service (DDoS) attack network. Discovered by Akamai’s Security... The post New botnet malware exploits zero-day CVE-2023-49897 flaw in routers appeared first on Penetration Testing.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Bleeping Computer
DECEMBER 8, 2023
A law enforcement operation is rumored to be behind an outage affecting ALPHV ransomware gang's websites over the last 30 hours.

Security Boulevard
DECEMBER 8, 2023
Learn six top tips for great holistic AppSec and software supply chain security. The post Six Top Tips For Holistic AppSec and Software Supply Chain Security appeared first on Mend. The post Six Top Tips For Holistic AppSec and Software Supply Chain Security appeared first on Security Boulevard.

Bleeping Computer
DECEMBER 8, 2023
Kentucky health system Norton Healthcare has confirmed that a ransomware attack in May exposed personal information belonging to patients, employees, and dependents. [.

Security Affairs
DECEMBER 8, 2023
Anatoly Legkodymov, the founder of the Bitzlato cryptocurrency exchange has pleaded in a money-laundering scheme. Anatoly Legkodymov (41) (aka Anatolii Legkodymov, Gandalf, and Tolik), the Russian founder of the unlicensed Bitzlato cryptocurrency exchange, has pleaded guilty in a money-laundering scheme. The police arrested Legkodymov in Miami in January, he was charged in a U.S. federal court with conducting a money-transmitting business that transported and transmitted illicit funds and that f

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Bleeping Computer
DECEMBER 8, 2023
Amazon's Customer Protection and Enforcement team has taken legal action against an underground store refund scheme that has resulted in the theft of millions of dollars worth of products from Amazon's online platforms. [.

The Hacker News
DECEMBER 8, 2023
Ransomware attacks have become a significant and pervasive threat in the ever-evolving realm of cybersecurity. Among the various iterations of ransomware, one trend that has gained prominence is Ransomware-as-a-Service (RaaS). This alarming development has transformed the cybercrime landscape, enabling individuals with limited technical expertise to carry out devastating attacks.

Malwarebytes
DECEMBER 8, 2023
Meta has announced Purple Llama, a project that aims to “bring together tools and evaluations to help the community build responsibly with open generative AI models.” Generative Artificial Intelligence (AI) models have been around for years and their main function, compared to older AI models is that they can process more types of input.

The Hacker News
DECEMBER 8, 2023
WordPress has released version 6.4.2 with a patch for a critical security flaw that could be exploited by threat actors by combining it with another bug to execute arbitrary PHP code on vulnerable sites.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.

Graham Cluley
DECEMBER 8, 2023
Two men have been charged with hacking into computer networks in the United States, UK, other NATO countries, and Ukraine, on behalf of the Russian government. Read more in my article on the Hot for Security blog.

Heimadal Security
DECEMBER 8, 2023
The Black Cat/AlphV ransomware gang claimed to have targeted California-based accounting software provider Tipalti. This alleged cyberattack raised concerns, particularly as the gang started threatening several high-profile Tipalti clients, including Roblox, Twitch, and more. Despite requests for comment, Tipalti’s initial response came through a Monday statement on social media, acknowledging the claim and emphasizing their […] The post Tipalti Is Investigating Alleged Ransomware At

The Hacker News
DECEMBER 8, 2023
The North Korean threat actor known as Kimsuky has been observed targeting research institutes in South Korea as part of a spear-phishing campaign with the ultimate goal of distributing backdoors on compromised systems.

Penetration Testing
DECEMBER 8, 2023
Microsoft has released a new update for Microsoft Edge Stable Channel (Version 120.0.2210.61) that addresses several critical security vulnerabilities. These vulnerabilities could allow attackers to remotely execute code, gain elevated privileges, or disclose sensitive... The post Patch Your Edge Now: Critical Sandbox Escape Vulnerability (CVE-2023-35618) appeared first on Penetration Testing.

Speaker: William Hord, Vice President of ERM Services
A well-defined change management process is critical to minimizing the impact that change has on your organization. Leveraging the data that your ERM program already contains is an effective way to help create and manage the overall change management process within your organization. Your ERM program generally assesses and maintains detailed information related to strategy, operations, and the remediation plans needed to mitigate the impact on the organization.

The Hacker News
DECEMBER 8, 2023
Unauthorized websites distributing trojanized versions of cracked software have been found to infect Apple macOS users with a new Trojan-Proxy malware.

Security Boulevard
DECEMBER 8, 2023
TA446’s new TTPs: “Star Blizzard” FSB team called out by Five Eyes governments (again). The post Russian FSB Targets US and UK Politicians in Sneaky Spear-Phish Plan appeared first on Security Boulevard.

InfoWorld on Security
DECEMBER 8, 2023
Meta has introduced Purple Llama, a project dedicated to creating open-source tools for developers to evaluate and boost the trustworthiness and safety of generative AI models before they are used publicly. Meta emphasized the need for collaborative efforts in ensuring AI safety, stating that AI challenges cannot be tackled in isolation. The company said the goal of Purple Llama is to establish a shared foundation for developing safer genAI as concerns mount about large language models and other

SecureBlitz
DECEMBER 8, 2023
Check out our gaming guide. In the dynamic realm of technology, gaming stands as a unique fusion of entertainment, education, and innovation. From the pixelated adventures of arcade classics to the breathtaking worlds of modern AAA titles, gaming has captivated millions of players across all demographics, transcending cultural and linguistic barriers to become a global […] The post Essential Gaming Guide: Mastering Cybersecurity in the Digital Arena appeared first on SecureBlitz Cybersecur

Speaker: William Hord, Senior VP of Risk & Professional Services
Enterprise Risk Management (ERM) is critical for industry growth in today’s fast-paced and ever-changing risk landscape. When building your ERM program foundation, you need to answer questions like: Do we have robust board and management support? Do we understand and articulate our bank’s risk appetite and how that impacts our business units? How are we measuring and rating our risk impact, likelihood, and controls to mitigate our risk?
Let's personalize your content