The Story of Colossus
Schneier on Security
MAY 6, 2021
Nice video of a talk by Chris Shore on the history of Colossus.

Schneier on Security
MAY 6, 2021
Nice video of a talk by Chris Shore on the history of Colossus.

Adam Shostack
MAY 6, 2021
Apple has released (or I’ve just come across) a document Device and Data Access when Personal Safety is At Risk. Apple makes it easy to connect and share your life with the people closest to you. What you share, and whom you share it with, is up to you — including the decision to make changes to better protect your information or personal safety.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
MAY 6, 2021
Scientists find that blaming employees is counterproductive and suggest creating a safe environment for people to admit their mistakes and learn from them. One company already puts that into practice.

We Live Security
MAY 6, 2021
Millions of Brits could be at risk of cyberattacks due to poor default passwords and a lack of firmware updates. The post Popular routers found vulnerable to hacker attacks appeared first on WeLiveSecurity.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Tech Republic Security
MAY 6, 2021
Patched on Qualcomm's end, the flaw could allow attackers to access your call history and text messages and eavesdrop on your phone conversations, says Check Point Research.

Malwarebytes
MAY 6, 2021
Most of our readers are well aware of the fact that the big tech corporations, especially those that run social media know a great deal about us and our behavior. But it rarely hits home how much personal data they have about us and how they can guess, quite correctly, even more. Lots more. Signal came up with an idea to drive that point home. A simple but very effective idea, nothing short of genius.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

SecureList
MAY 6, 2021
Windows rootkits, especially those operating in kernel space, are pieces of malware infamous for their near absolute power in the operating system. Usually deployed as drivers, such implants have high privileges in the system, allowing them to intercept and potentially tamper with core I/O operations conducted by the underlying OS, like reading or writing to files or processing incoming and outgoing network packets.

Tech Republic Security
MAY 6, 2021
Expert discusses the importance of keeping internal computer credentials as safe as your passwords. The need for security never goes away.

Security Boulevard
MAY 6, 2021
Having a framework for security helps organizations identify what is missing and what is needed for their existing security architecture. A recent article in Dark Reading covered some of the cyber security frameworks that are available. The post Choosing a Cyber Security Framework appeared first on K2io. The post Choosing a Cyber Security Framework appeared first on Security Boulevard.
Bleeping Computer
MAY 6, 2021
Attackers can use a newly disclosed domain name server (DNS) vulnerability publicly known as TsuNAME as an amplification vector in large-scale reflection-based distributed denial of service (DDoS) attacks targeting authoritative DNS servers. [.].

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Security Boulevard
MAY 6, 2021
Ransomware Attacks Double and Evolve Year-on-year! Security researchers have uncovered that year-on-year ransomware attacks are doubling in number. According to a report from. The post Top 5 Ransomware Attacks to Watch Out for in 2021 appeared first on Kratikal Blog. The post Top 5 Ransomware Attacks to Watch Out for in 2021 appeared first on Security Boulevard.

Digital Shadows
MAY 6, 2021
Note: This blog is an overview of password history and best practices for individuals in honor of World Password Day, The post Creating Security-Aware Passwords first appeared on Digital Shadows.

Security Boulevard
MAY 6, 2021
Mobile device management (MDM) deployments haven’t exactly put the kibosh on threats to financial services. In fact, even while MDM adoption rose 50%, quarterly exposure to phishing between 2019 and 2020 jumped by 125%, according to the Lookout Financial Services Threat Report. That’s certainly noteworthy, but the 400% increase in malware and app exposure is.

Thales Cloud Protection & Licensing
MAY 6, 2021
Harness the Power of Recurring Business Models. jstewart. Thu, 05/06/2021 - 16:01. The experts call it many things: digital transformation, servitization strategies, and business model diversification. Regardless of the name, the end result is the same: recurring revenues. During the Covid-19 crisis, companies that have successfully invested and executed recurring business models have proven more resilient than those who have not.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
MAY 6, 2021
Cybersecurity is not a One-Stop-Shop. Boris Johnson announced the Government’s roadmap to lift Coronavirus restrictions for both businesses and the general public earlier in February, and since then, this has provided a glimmer of hope for many across the country. However, since the start of the pandemic, the way business is conducted has changed permanently, with many workforces wanting to continue to work remotely as lockdowns and restrictions ease over time.

Bleeping Computer
MAY 6, 2021
A student's attempt to pirate an expensive data visualization software led to a full-blown Ryuk ransomware attack at a European biomolecular research institute. [.].

Security Boulevard
MAY 6, 2021
In a recently released report sponsored by HP, Nation States, Cyberconflict and the Web of Profit, Dr. Mike McGuire, senior lecturer in criminology at the University of Surrey, claims a 100% rise in nation-state cyberincidents between 2017 and 2020. Furthermore, the report notes there have been 27 known nation-state supply chain attacks in this same.

Bleeping Computer
MAY 6, 2021
A high severity security vulnerability found in Qualcomm's Mobile Station Modem (MSM) chips (including the latest 5G-capable versions) could enable attackers to access mobile phone users' text messages, call history, and listen in on their conversations. [.].

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

We Live Security
MAY 6, 2021
How witches, wizards and superheroes can help your kids stay safe from cyber-villains, plus other parenting hacks to encourage your children to use secure passwords. The post Fantastic passwords and where your children can find them appeared first on WeLiveSecurity.

Tech Republic Security
MAY 6, 2021
On world password day, data from Onfido serves as a reminder that most people don't follow password recommendations, probably never will, and that means it's time to find a new security standard.
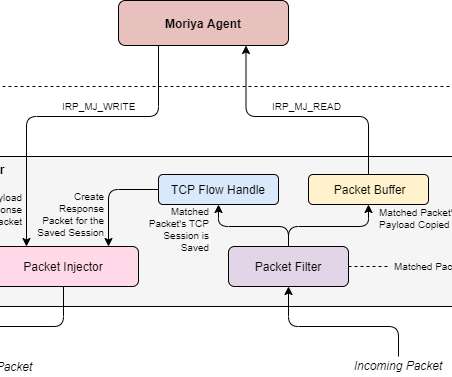
Security Affairs
MAY 6, 2021
Experts spotted a new malware, dubbed Moriya rootkit, that targets Windows systems as part of cyberespionage campaign dubbed TunnelSnake. An unclassified threat actor employed a new stealthy malware, dubbed Moriya rootkit, to compromise Windows systems. Kaspersky experts who uncovered the threat speculate the attacks are likely part of an ongoing espionage campaign dubbed TunnelSnake that has been active since at least 2018.

CyberSecurity Insiders
MAY 6, 2021
If anyone wants their online activity to be secure and private, password usage helps them in doing so; as it blocks unauthorized access to a service and access to personal information. For website business, the owners of these web portals have 2 primary concerns- one is to protect their sensitive consumer and business data and the other is to isolate them from prevailing malware and viruses from attacking their website.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Graham Cluley
MAY 6, 2021
The US Defense Department and third-party military contractors are being advised to strengthen the security of their operational technology (OT) in the wake of security breaches, such as the SolarWinds supply chain attack. Read more in my article on the Tripwire State of Security blog.

Hot for Security
MAY 6, 2021
Cybersecurity teams have historically been hampered by lax IT budgets, a shortage of skills and alert fatigue, which leaves security analysts overwhelmed by the sheer amount of alerts to parse. However, retention issues also plague the industry. And according to a recent study, the increasing volume of cyber-attacks in recent years is directly responsible for this syndrome.

Heimadal Security
MAY 6, 2021
DarkSide is a ransomware program that began attacking organizations worldwide in August 2020. Originally discovered by MalwareHunterTeam, DarkSide ransomware is described as a high-risk ransomware-type virus that seems to be operated by former affiliates of other ransomware campaigns. Having announced themselves through a ‘press release’, as disclosed in BleepingComputer, this ransomware has already collected million-dollar payments […].

Security Boulevard
MAY 6, 2021
Cloud computing has accompanied a new borderless work world, which boosts the free flow of information and open collaborations. This has allowed companies to be more productive and has made. The post 5 Top Cloud Security Threats and Tips to Mitigate Them appeared first on Indusface. The post 5 Top Cloud Security Threats and Tips to Mitigate Them appeared first on Security Boulevard.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Bleeping Computer
MAY 6, 2021
Google strives to push all its users to start using two-factor authentication (2FA), which can block attackers from taking control of their accounts using compromised credentials or guessing their passwords. [.].

Security Boulevard
MAY 6, 2021
Bruce Gibson offers an overview of what he's observed across industries to be best practices for securing public cloud infrastructure. The post Best Practices for Securing Public Cloud Infrastructure appeared first on Ermetic. The post Best Practices for Securing Public Cloud Infrastructure appeared first on Security Boulevard.
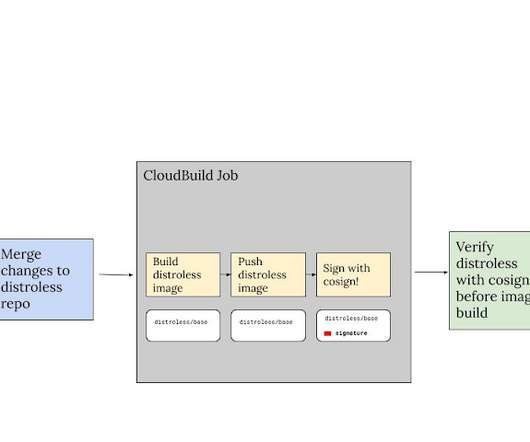
Google Security
MAY 6, 2021
Posted by Priya Wadhwa, Google Open Source Security Team With over 16 million pulls per month, Google’s `distroless` base images are widely used and depended on by large projects like Kubernetes and Istio. These minimal images don’t include common tools like shells or package managers, making their attack surface (and download size!) smaller than traditional base images such as `ubuntu` or `alpine`.

CSO Magazine
MAY 6, 2021
On March 2, 2021 Microsoft detected multiple zero-day exploits being used to attack on-premises versions of Microsoft Exchange Server. Over the next few days, over 30,000 organizations in the US were attacked as hackers used several Exchange vulnerabilities to gain access to email accounts and install web shell malware , giving the cybercriminals ongoing administrative access to the victims' servers. [ Related reading: 9 tips to detect and prevent web shell attacks on Windows networks | Sign up

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content