How project managers can help companies better navigate security risks from COVID-19
Tech Republic Security
SEPTEMBER 3, 2020
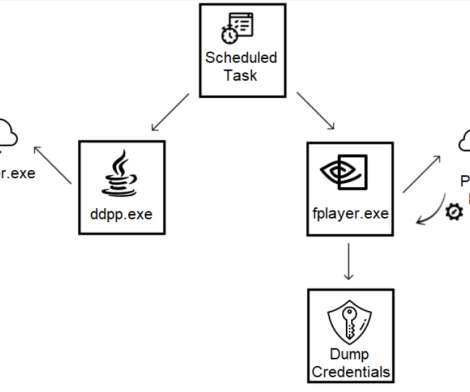
Social distancing and remote working during COVID-19 have increased cybersecurity risks for companies worldwide, increasing the need for project managers to work on more security-related efforts.








































Let's personalize your content