Patch Tuesday, December 2024 Edition
Krebs on Security
DECEMBER 10, 2024
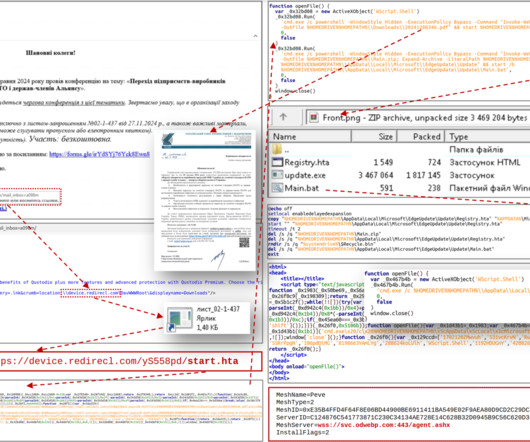
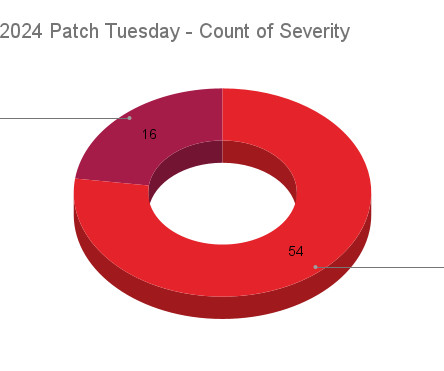
Microsoft today released updates to plug at least 70 security holes in Windows and Windows software, including one vulnerability that is already being exploited in active attacks. The zero-day seeing exploitation involves CVE-2024-49138 , a security weakness in the Windows Common Log File System (CLFS) driver — used by applications to write transaction logs — that could let an authenticated attacker gain “system” level privileges on a vulnerable Windows device.








































Let's personalize your content