White House Announces AI Cybersecurity Challenge
Schneier on Security
AUGUST 21, 2023
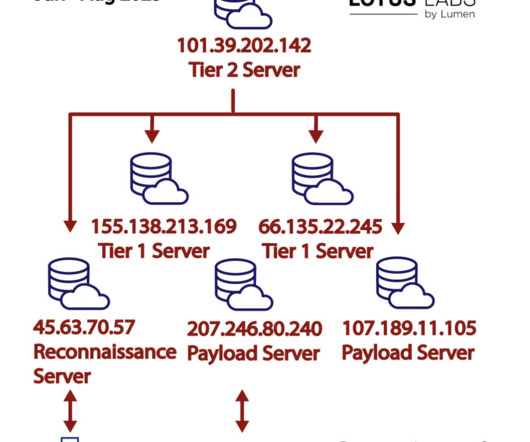
At Black Hat last week, the White House announced an AI Cyber Challenge. Gizmodo reports : The new AI cyber challenge (which is being abbreviated “AIxCC”) will have a number of different phases. Interested would-be competitors can now submit their proposals to the Small Business Innovation Research program for evaluation and, eventually, selected teams will participate in a 2024 “qualifying event.” During that event, the top 20 teams will be invited to a semifinal competi






































Let's personalize your content