Phishing Domains Tanked After Meta Sued Freenom
Krebs on Security
MAY 26, 2023
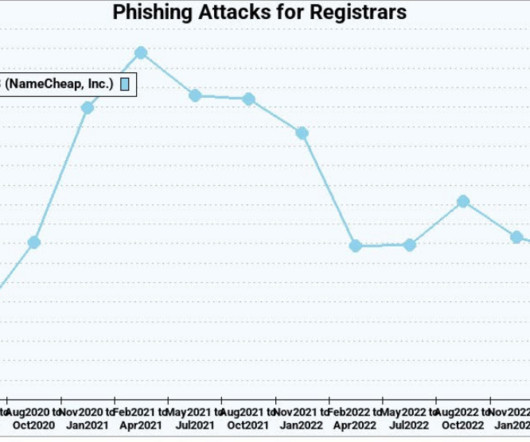
The number of phishing websites tied to domain name registrar Freenom dropped precipitously in the months surrounding a recent lawsuit from social networking giant Meta , which alleged the free domain name provider has a long history of ignoring abuse complaints about phishing websites while monetizing traffic to those abusive domains. The volume of phishing websites registered through Freenom dropped considerably since the registrar was sued by Meta.







































Let's personalize your content