Many Cyber Attacks Begin by Breaking Human Trust
Lohrman on Security
OCTOBER 1, 2023
Sophisticated social engineering attacks have led to hundreds of data breaches this year. What can be done? And what new resources can help?
Lohrman on Security
OCTOBER 1, 2023
Sophisticated social engineering attacks have led to hundreds of data breaches this year. What can be done? And what new resources can help?
Troy Hunt
OCTOBER 4, 2023
Imagine you wanted to buy some s**t on the internet. Not the metaphorical kind in terms of "I bought some random s**t online", but literal s**t. Turds. Faeces. The kind of thing you never would have thought possible to buy online until. Shitexpress came along. Here's a service that enables you to send an actual piece of smelly s**t to "An irritating colleague.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
OCTOBER 3, 2023
Turns out pumps at gas stations are controlled via Bluetooth, and that the connections are insecure. No details in the article, but it seems that it’s easy to take control of the pump and have it dispense gas without requiring payment. It’s a complicated crime to monetize, though. You need to sell access to the gas pump to others.

Joseph Steinberg
OCTOBER 4, 2023
CyberSecurity and Artificial Intelligence Expert , Joseph Steinberg, will keynote the upcoming Securing the Future: Cloud, Cybersecurity, and AI Summit , taking place on Wednesday, October 11, 2023, in Pennsylvania, USA. The summit, sponsored by Avail Technology Solutions, will allow participants to learn about the latest advancements and trends in cloud technology, cybersecurity practices, and the exciting world of Artificial Intelligence (AI) — topics that Steinberg will cover in his key

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Krebs on Security
OCTOBER 2, 2023
Many organizations — including quite a few Fortune 500 firms — have exposed web links that allow anyone to initiate a Zoom video conference meeting as a valid employee. These company-specific Zoom links, which include a permanent user ID number and an embedded passcode, can work indefinitely and expose an organization’s employees, customers or partners to phishing and other social engineering attacks.

The Last Watchdog
OCTOBER 4, 2023
Something simply must be done to slow, and ultimately reverse, attack surface expansion. Related: What Cisco’s buyout of Splunk really signals We’re in the midst of driving towards a dramatically scaled-up and increasingly connected digital ecosystem. Companies are obsessed with leveraging cloud-hosted IT infrastructure and the speedy software development and deployment that goes along with that.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
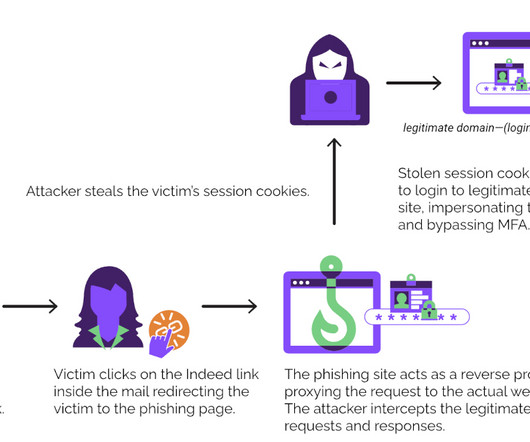
Tech Republic Security
OCTOBER 6, 2023
Microsoft, the Dark Web and the name John Malkovich all factor into this EvilProxy phishing attack. The good news is there are steps IT can take to mitigate this security threat.

Krebs on Security
SEPTEMBER 30, 2023
Earlier this week, KrebsOnSecurity revealed that the darknet website for the Snatch ransomware group was leaking data about its users and the crime gang’s internal operations. Today, we’ll take a closer look at the history of Snatch, its alleged founder, and their claims that everyone has confused them with a different, older ransomware group by the same name.

The Last Watchdog
OCTOBER 5, 2023
Editor’s note: I recently had the chance to participate in a discussion about the overall state of privacy and cybersecurity with Erin Kapczynski, OneRep’s senior vice president of B2B marketing. OneRep provides a consumer service that scrubs your personal information from Google and dozens of privacy-breaching websites. Here is Erin’s Q&A column, which originally went live on OneRep’s well-done blog.

Schneier on Security
OCTOBER 6, 2023
Well designed and well timed deepfake or two Slovakian politicians discussing how to rig the election: Šimečka and Denník N immediately denounced the audio as fake. The fact-checking department of news agency AFP said the audio showed signs of being manipulated using AI. But the recording was posted during a 48-hour moratorium ahead of the polls opening, during which media outlets and politicians are supposed to stay silent.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Tech Republic Security
OCTOBER 3, 2023
It doesn’t matter whether your organization is a huge multinational business enterprise or a one-person operation. At some point, your computer networks and systems will be attacked by someone with criminal intent. Cybersecurity attacks, in all their various forms, are inevitable and relentless. This quick glossary from TechRepublic Premium explains the terminology behind the most.

Thales Cloud Protection & Licensing
OCTOBER 2, 2023
Cybersecurity Awareness Month 2023 – What it is and why we should be aware madhav Tue, 10/03/2023 - 05:33 The inception of Cybersecurity Awareness Month in 2004 came at a critical juncture in our technological history. As we are well and truly in the digital-first age, the need for robust cybersecurity measures is glaringly evident. Though significant, the early days' threats vastly differed from today's sophisticated cyberattacks.

The Last Watchdog
OCTOBER 2, 2023
Surrounded by the invisible hum of electromagnetic energy, we’ve harnessed its power to fuel our technological marvels for decades. Related: MSFT CEO calls for regulating facial recognition tech Tesla’s visionary insights from 1900 hinted at the potential, and today, we bask in the glow of interconnected networks supporting our digital lives.

Schneier on Security
OCTOBER 4, 2023
Malicious ads are creeping into chatbots.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Bleeping Computer
OCTOBER 6, 2023
23andMe has confirmed to BleepingComputer that it is aware of user data from its platform circulating on hacker forums and attributes the leak to a credential-stuffing attack. [.

WIRED Threat Level
OCTOBER 6, 2023
At least a million data points from 23andMe accounts appear to have been exposed on BreachForums. While the scale of the campaign is unknown, 23andMe says it's working to verify the data.

Tech Republic Security
OCTOBER 3, 2023
This high-speed, unlimited VPN offers quality connections all over the globe. Get huge savings now when you sign up for life at TechRepublic Academy.

Malwarebytes
OCTOBER 2, 2023
Post anything publicly on Facebook and Instagram? Meta has likely been using those posts to train its AI, according to the company's top policy executive. In an interview with Reuters , Meta President of Global Affairs Nick Clegg said the company used the public posts to train the LLM (large language model) that feeds into its new Meta AI virtual assistant.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Bleeping Computer
OCTOBER 3, 2023
A new Linux vulnerability, known as 'Looney Tunables' and tracked as CVE-2023-4911, enables local attackers to gain root privileges by exploiting a buffer overflow weakness in the GNU C Library's ld.so dynamic loader. [.

WIRED Threat Level
OCTOBER 4, 2023
Elon Musk’s brain-chip startup conducted years of tests at UC Davis, a public university. A WIRED investigation reveals how Neuralink and the university keep the grisly images of test subjects hidden.

Tech Republic Security
OCTOBER 6, 2023
Read our comprehensive review of IPVanish VPN. Discover its features, pricing, and more to determine if it meets your online security and privacy needs.
Security Affairs
OCTOBER 5, 2023
NATO is investigating claims that a group called SiegedSec has breached its systems and leaked a cache of unclassified documents online. NATO announced it is investigating claims that a politically motivated threat actor called SiegedSec has breached its systems and leaked unclassified documents online. “NATO cyber experts are actively addressing incidents affecting some unclassified NATO websites,” reads a statement issued by s NATO official to media outlets.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Bleeping Computer
OCTOBER 2, 2023
For Windows users who frequently use the TorBrowser, there's been a pressing concern. Recent versions of the TorBrowser, specifically because of the tor.exe file it contained, were being flagged as potential threats by Windows Defender. [.
Graham Cluley
OCTOBER 6, 2023
A joint advisory from the United States's National Security Agency (NSA) and Cybersecurity and Infrastructure Security Agency (CISA) has shone a light on the top ten most common cybersecurity misconfigurations found in large private and public organisations. Read more in my article on the Tripwire State of Security blog.

Tech Republic Security
OCTOBER 2, 2023
Don't be surprised when connecting multiple iPhones to one Apple ID. Learn how to prevent common errors and issues with this guide.

Dark Reading
OCTOBER 4, 2023
The flaw poses a significant risk of unauthorized data access, system alterations, potential data theft, and complete takeover of vulnerable systems, especially in the IoT and embedded computing space.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.

Bleeping Computer
OCTOBER 4, 2023
Sony Interactive Entertainment (Sony) has notified current and former employees and their family members about a cybersecurity breach that exposed personal information. [.

Security Affairs
OCTOBER 4, 2023
Sony Interactive Entertainment has notified current and former employees and their family members about a data breach. Sony Interactive Entertainment (SIE) has notified current and former employees and their family members about a data breach that exposed their personal information. Sony notified about 6,800 individuals, it confirmed that the security breach was the result of the exploitation of the zero-day vulnerability CVE-2023-34362 in the MOVEit Transfer platform.
Tech Republic Security
OCTOBER 4, 2023
AdGuard gets rid of ads and provides an extra layer of protection on multiple devices. Through October 15th only, it's just $25 for life.

Security Boulevard
OCTOBER 6, 2023
Apple’s embarrassing regression: iOS 17.0.3 fixes yet more nasty zero-days (and the overheating bug). The post iPhone/iPad Warning: Update Now to Avoid Zero-Day Pain appeared first on Security Boulevard.

Speaker: William Hord, Vice President of ERM Services
A well-defined change management process is critical to minimizing the impact that change has on your organization. Leveraging the data that your ERM program already contains is an effective way to help create and manage the overall change management process within your organization. Your ERM program generally assesses and maintains detailed information related to strategy, operations, and the remediation plans needed to mitigate the impact on the organization.
Let's personalize your content