Weekly Update 167
Troy Hunt
DECEMBER 1, 2019
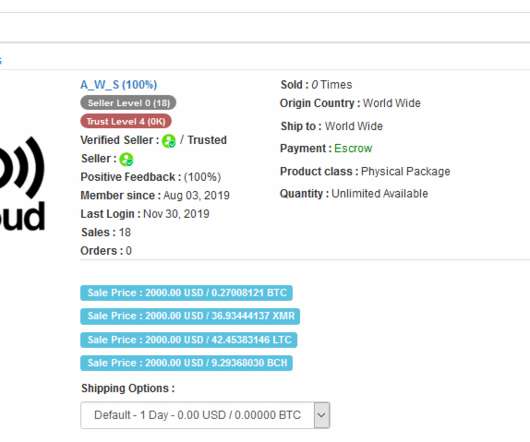
It's summer! Yes, I know it's back to front for many of you but Dec 1 means it's sunnier than ever here. Regardless, this week I've been at DDD in Brisbane, written my 10 year old son Ari and I running kids coding clubs in Oslo (cold) and London (rainy) next month and the Swiss gov being on-boarded onto HIBP. Plus there's this week's sponsor IVPN and how tracking ain't tracking (that may be a bit of an old Aussieism ).




































Let's personalize your content