New Sophisticated Malware
Schneier on Security
MAY 4, 2022
Mandiant is reporting on a new botnet. The group, which security firm Mandiant is calling UNC3524, has spent the past 18 months burrowing into victims’ networks with unusual stealth.

Schneier on Security
MAY 4, 2022
Mandiant is reporting on a new botnet. The group, which security firm Mandiant is calling UNC3524, has spent the past 18 months burrowing into victims’ networks with unusual stealth.

Krebs on Security
MAY 2, 2022
Image: Proxima Studios, via Shutterstock.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Troy Hunt
MAY 6, 2022
It's back to business as usual with more data breaches, more poor handling of them and more IoT pain. I think on all those fronts there's a part of me that just likes the challenge and the opportunity to fix a broken thing.

The Last Watchdog
MAY 2, 2022
Potable water and wastewater management is a top priority for cybersecurity professionals and the Biden administration alike. With new regulations and funding, companies must find the best way to implement and manage cybersecurity to protect these systems. Related: Keeping critical systems patched.

Speaker: Karl Camilleri, Cloud Services Product Manager at phoenixNAP
Through a detailed analysis of major attacks and their consequences, Karl Camilleri, Cloud Services Product Manager at phoenixNAP, will discuss the state of ransomware and future predictions, as well as provide best practices for attack prevention and recovery.
Lohrman on Security
MAY 1, 2022
Criminals are using stolen information to imitate the police and scam both companies and individuals. Here’s what you need to know
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

The Last Watchdog
MAY 5, 2022
Ransomware? I think you may have heard of it, isn’t the news full of it? Well, the stats are even scarier with over 50% increase in ransomware attacks in 2021, compared to 2020. Related: Make it costly for cybercriminals. The media paid close attention to ransomware attacks last year, as they had a significant impact on Colonial Pipeline, the nation’s largest fuel distributor, and JBS, the nation’s largest meat distributor.
Schneier on Security
MAY 5, 2022
Cloudflare is reporting a large DDoS attack against an unnamed company “operating a crypto launchpad.” ” While this isn’t the largest application-layer attack we’ve seen , it is the largest we’ve seen over HTTP S.
Cisco CSR
MAY 5, 2022
Customers globally are requesting - and often requiring - SaaS providers to demonstrate their commitment to security, availability, confidentiality, and privacy. While attaining global security certifications has become table-stakes for many to do business, it’s no easy feat.
We Live Security
MAY 3, 2022
Organizations need to get better at mitigating threats from unknown vulnerabilities, especially as both state-backed operatives and financially-motivated cybercriminals are increasing their activity. The post What’s behind the record‑high number of zero days? appeared first on WeLiveSecurity.

Speaker: Ronald Eddings, Cybersecurity Expert and Podcaster
In this webinar, Ronald Eddings, Cybersecurity Expert, will outline the relationship between SaaS apps and IT & security teams, along with several actionable solutions to overcome the new difficulties facing your organization.

Security Boulevard
MAY 4, 2022
Back on May 25, 2018, the European Union’s General Data Protection Regulation (GDPR) came into effect, meaning all organizations that offer goods or services to European Union residents, or collect consumer data within the region, are now required to comply with the regulation.
CyberSecurity Insiders
MAY 2, 2022
Executive summary. 2022 has experienced an increase in the number of wiper variants targeting Ukrainian entities.
Cisco CSR
MAY 4, 2022
Cisco is pleased to announce a new addition to the Forensic Investigation Procedures for First Responders series of documents that will help customers and partners triage Cisco products that are suspected of being tampered with or compromised.

Dark Reading
MAY 3, 2022
The same infrastructure traced back to Russian-speaking threat group Nobelium is being used to set up misspelled domain names, presaging impersonation attacks bent on credential harvesting, analysts say

Speaker: P. Andrew Sjogren, Sr. Product Marketing Manager at Very Good Security, Matt Doka, Co-Founder and CTO of Fivestars, and Steve Andrews, President & CEO of the Western Bankers Association
In this webinar, we have a great set of panelists who will take you through how Zero Data strategies can be used as part of a well-rounded compliance and security approach, and get you to market much sooner by also allowing for payment optimization. They’ll share how to grow your business faster and minimize costs for both security and compliance
Security Boulevard
MAY 1, 2022
In the past, I’ve written about digital privacy and how much data we leak through our day to day interactions. I think this is an important topic to consider and really focus on and it is an element of cybersecurity at both the enterprise and personal level that isn’t discussed enough.
CyberSecurity Insiders
MAY 2, 2022
Microsoft’s Digital Security Unit has confirmed that Russian cyber attacks on Ukraine were timed in such a way that they coincided with the timing of military strikes.
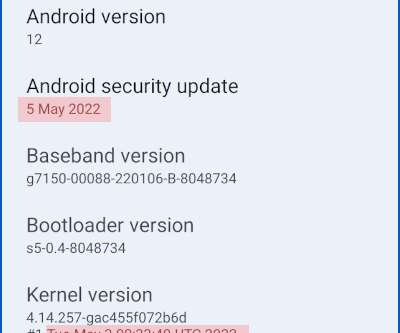
Naked Security
MAY 4, 2022
Android May 2022 updates are out - with some critical fixes in some critical places. Learn more. Android Google Vulnerability critical Patch update vulnerability

Dark Reading
MAY 4, 2022
Companies see AI-powered cybersecurity tools and systems as the future, but at present nearly 90% of them say they face significant hurdles in making use of them

Speaker: Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies
Now that companies are slowly allowing employees to return to work at the office, it's time to re-evaluate your company’s posture towards privacy and security. Join Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies, for a discussion that will focus on compliance and the types of privacy and security measures your company should be aware of, as well as tips and methods for implementing these measures.
Security Boulevard
MAY 2, 2022
Twenty years ago, Bill Gates foresaw the security threats looming as new technologies were introduced and threat actors were ramping up their efforts. He urged for including security development at every stage of the software life cycle in his company’s products.
CyberSecurity Insiders
MAY 1, 2022
A Texas school district has hit Google headlines as one of its employees was caught mining cryptocurrency without permission of the school management or the government officials.
The Hacker News
MAY 2, 2022
A Chinese-aligned cyberespionage group has been observed striking the telecommunication sector in Central Asia with versions of malware such as ShadowPad and PlugX.
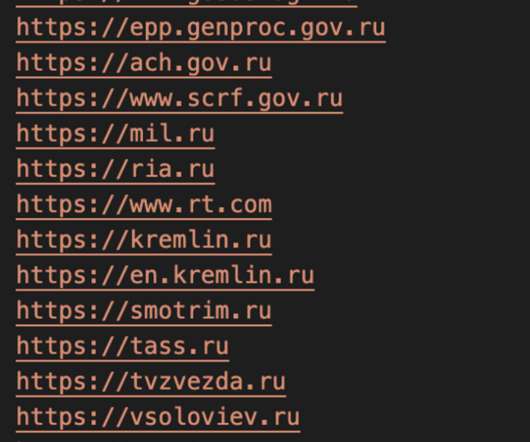
Security Affairs
MAY 4, 2022
Pro-Ukraine hackers are using Docker images to launch distributed denial-of-service (DDoS) attacks against a dozen Russian and Belarusian websites.
Cisco CSR
MAY 3, 2022
The Public Cloud and Security Responsibility. Across many businesses, leveraging services offered and hosted by public cloud providers such as AWS proves to be extremely advantageous for both improving operational efficiencies, cost savings, scaling, and for security.
CyberSecurity Insiders
MAY 1, 2022
All these days we have been discussing Distributed Denial of Service attacks aka Ddos attacks and the massive amounts of fake traffic they create to network disruptions in corporate and government networks.
The Hacker News
MAY 2, 2022
Cybersecurity researchers have disclosed an unpatched security vulnerability that could pose a serious risk to IoT products.
eSecurity Planet
MAY 3, 2022
Databases contain some of the most critical data in enterprises, so vulnerabilities in them are serious issues.
Security Affairs
MAY 2, 2022
IoT gizmos make our lives easier, but we forget that these doohickeys are IP endpoints that act as mini-radios. They continuously send and receive data via the internet and can be the easiest way for a hacker to access your home network.
CyberSecurity Insiders
MAY 5, 2022
World Password Day is celebrated in May every year and is being done since 2013 as a group of Cybersecurity Professionals declared the first Thursday of May every year as the day to celebrate as the security day of our online lives.

The Hacker News
MAY 4, 2022
Cisco Systems on Wednesday shipped security patches to contain three flaws impacting its Enterprise NFV Infrastructure Software (NFVIS) that could permit an attacker to fully compromise and take control over the hosts.

Security Boulevard
MAY 3, 2022
The Department of Defense (DoD) is planning to release an Interim Rule on the CMMC framework by May 2023, according to Stacy Bostjanick, director of the CMMC (Cybersecurity Maturity Model Certification) program for the DoD.
Security Affairs
MAY 3, 2022
China-linked Curious Gorge APT is targeting Russian government agencies, Google Threat Analysis Group (TAG) warns.
CyberSecurity Insiders
MAY 5, 2022
As a business, fraud is something to be aware of and to put preventative measures in place where possible. Just like cybercrime, online fraud can happen to anyone - it doesn’t discriminate regardless of whether you’re a big or small company. .
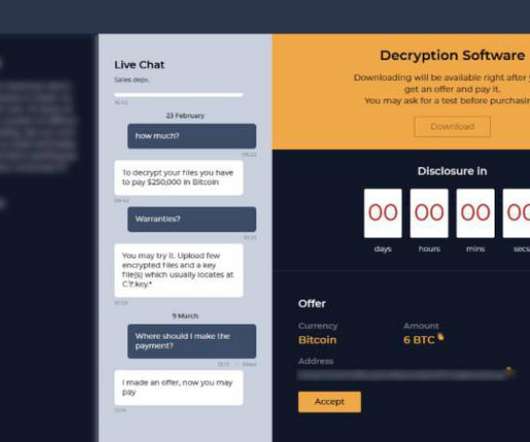
The Hacker News
MAY 3, 2022
An analysis of four months of chat logs spanning more than 40 conversations between the operators of Conti and Hive ransomware and their victims has offered an insight into the groups' inner workings and their negotiation techniques.
Let's personalize your content