IRS Will Soon Require Selfies for Online Access
Krebs on Security
JANUARY 19, 2022
If you created an online account to manage your tax records with the U.S. Internal Revenue Service (IRS), those login credentials will cease to work later this year.

Krebs on Security
JANUARY 19, 2022
If you created an online account to manage your tax records with the U.S. Internal Revenue Service (IRS), those login credentials will cease to work later this year.
Joseph Steinberg
JANUARY 19, 2022
At some point in the not-so-distant future, quantum computers are going to pose a major threat to today’s encryption mechanisms and encrypted data.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Schneier on Security
JANUARY 18, 2022
Rolling Stone is reporting that the UK government has hired the M&C Saatchi advertising agency to launch an anti-encryption advertising campaign. Presumably they’ll lean heavily on the “think of the children!”
Troy Hunt
JANUARY 21, 2022
It's mostly breaches this week and that's mostly business as usual, except for one. I didn't know whether I should speak about the one that frankly, upset me, but I felt it would be somewhat disingenuous not to.

Speaker: Karl Camilleri, Cloud Services Product Manager at phoenixNAP
Through a detailed analysis of major attacks and their consequences, Karl Camilleri, Cloud Services Product Manager at phoenixNAP, will discuss the state of ransomware and future predictions, as well as provide best practices for attack prevention and recovery.
Joseph Steinberg
JANUARY 20, 2022
Zero Trust. A seemingly simple term that appears in pitches sent to me several times a day by cybersecurity product and services vendors that are seeking media exposure.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

The Last Watchdog
JANUARY 18, 2022
After a gloomy start with its first three breach intensive quarters, 2021 has finally ended, and on a positive note. Related: Cybersecurity experts reflect on 2021. This conclusion is derived from an analysis of data taken from our data breach detection tool, Surfshark Alert , which comprises publicly available breached data sets to inform our users of potential threats.

Anton on Security
JANUARY 20, 2022
20 years of SIEM? On Jan 20, 2002 , exactly 20 years ago, I joined a “SIM” vendor that shall remain nameless, but is easy to figure out. That windy winter day in northern New Jersey definitely set my security career on a new course.

Lohrman on Security
JANUARY 16, 2022
There were new developments in 2021 regarding implanting microchips into humans. So what plans were announced for 2022? And just as important, what are the privacy and security ramifications
Schneier on Security
JANUARY 20, 2022
Last summer, the San Francisco police illegally used surveillance cameras at the George Floyd protests. The EFF is suing the police: This surveillance invaded the privacy of protesters, targeted people of color, and chills and deters participation and organizing for future protests.

Speaker: Ronald Eddings, Cybersecurity Expert and Podcaster
In this webinar, Ronald Eddings, Cybersecurity Expert, will outline the relationship between SaaS apps and IT & security teams, along with several actionable solutions to overcome the new difficulties facing your organization.
The Last Watchdog
JANUARY 17, 2022
A key CEO responsibility is reporting results that deliver on a company’s mission to shareholders. This reporting often requires a host of metrics that define success, like Annual Recurring Revenue and sales for software as a service (SaaS) companies. These are lagging indicators where the results follow behind the work required to achieve them. Related: Automating SecOps. Lagging indicators are separate from leading indicators that could include marketing leads, pipeline generation and demos.
Tech Republic Security
JANUARY 20, 2022
The Microsoft RDP vulnerability is a serious problem, but with a few caveats: It's been patched, and experts say it may be less likely to happen than it seems at first glance
The Hacker News
JANUARY 21, 2022
In yet another instance of software supply chain attack, dozens of WordPress themes and plugins hosted on a developer's website were backdoored with malicious code in the first half of September 2021 with the goal of infecting further sites.
Schneier on Security
JANUARY 19, 2022
Over the past few weeks, I’ve seen a bunch of writing about what seems to be fake COVID-19 testing sites. They take your name and info, and do a nose swab, but you never get test results.

Speaker: P. Andrew Sjogren, Sr. Product Marketing Manager at Very Good Security, Matt Doka, Co-Founder and CTO of Fivestars, and Steve Andrews, President & CEO of the Western Bankers Association
In this webinar, we have a great set of panelists who will take you through how Zero Data strategies can be used as part of a well-rounded compliance and security approach, and get you to market much sooner by also allowing for payment optimization. They’ll share how to grow your business faster and minimize costs for both security and compliance

The Last Watchdog
JANUARY 20, 2022
Looking back, 2021 was a breakout year for ransomware around the globe, with ransoms spiking to unprecedented multi-million dollar amounts. Related: Colonial Pipeline attack ups ransomware ante. All this while Endpoint Detection and Response system (EDR) installations are at an all-time high. EDR systems are supposed to protect IT system endpoints against these very malware, ransomware, and other types of malicious code.
Tech Republic Security
JANUARY 18, 2022
As more companies focus on digital adoption goals in 2022, finding security tools to detect malicious activity is top-of-mind for executives
Security Boulevard
JANUARY 21, 2022
China is mandating that athletes download and use a health and travel app when they attend the Winter Olympics next month. Citizen Lab examined the app and found it riddled with security holes.
Schneier on Security
JANUARY 17, 2022
Here’s a fascinating report: “ Bounty Everything: Hackers and the Making of the Global Bug Marketplace.”

Speaker: Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies
Now that companies are slowly allowing employees to return to work at the office, it's time to re-evaluate your company’s posture towards privacy and security. Join Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies, for a discussion that will focus on compliance and the types of privacy and security measures your company should be aware of, as well as tips and methods for implementing these measures.
Dark Reading
JANUARY 21, 2022
Threat actors from Eastern Europe seen expressing some concern about Russia being a safe place for them to continue operating, researchers say
Security Affairs
JANUARY 21, 2022
McAfee addressed a security flaw in its McAfee Agent software for Windows that allows running arbitrary code with SYSTEM privileges. McAfee (now Trellix) has addressed a high-severity vulnerability, tracked as CVE-2022-0166 , that resides in McAfee Agent software for Windows.
Security Boulevard
JANUARY 20, 2022
Despite your best efforts to prevent it, you get hit by a massive cyberattack. Maybe it’s a data breach; maybe a ransomware attack or maybe a supply chain disruption.
CyberSecurity Insiders
JANUARY 19, 2022
VirusTotal, an anti-malware solution provider, is now offering a service that can collect credentials stolen by malicious software aka malware.
Dark Reading
JANUARY 19, 2022
Among them: Explainable artificial intelligence (XAI) will improve the ways humans and AI interact, plus expect a shift in how organizations fight ransomware
We Live Security
JANUARY 18, 2022
ESET researchers take a deep look into recent attacks carried out by Donot Team throughout 2020 and 2021, targeting government and military entities in several South Asian countries. The post DoNot Go! Do not respawn! appeared first on WeLiveSecurity. ESET Research
Security Boulevard
JANUARY 20, 2022
Throughout its history, the tech industry has had to deal with constant change, increasingly complex architectures and security challenges. Security is a particularly deep well of concepts to navigate.
CyberSecurity Insiders
JANUARY 17, 2022
Microsoft has issued an official warning to all IT and not-for-profit organizations, along with some critical government organizations across Ukraine, that their digital infrastructure could be targeted by a dreaded data wiping malware campaign.

Dark Reading
JANUARY 19, 2022
No matter what cloud services you employ, you are still responsible for protecting the security of your data

We Live Security
JANUARY 17, 2022
Do you often take to social media to broadcast details about your job, employer or coworkers? Think before you share – less may be more. The post Social media in the workplace: Cybersecurity dos and don’ts for employees appeared first on WeLiveSecurity. Social Media
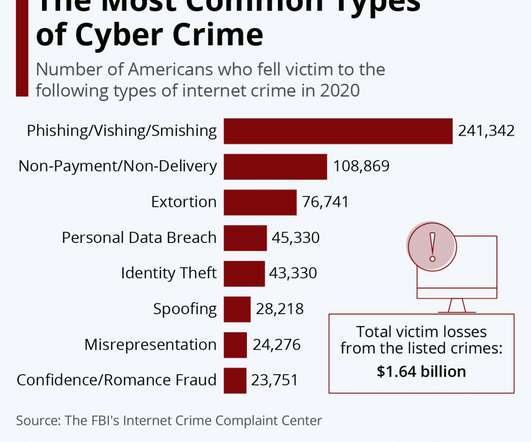
Security Boulevard
JANUARY 17, 2022
As per an article by The Hindu, 50,035 cases of cybercrime were reported in 2020, 11.8% more than in 2019 while 60.2% of cybercrimes were of fraud. Every organization or institution has some sort of information or data that needs to be protected.
The Hacker News
JANUARY 20, 2022
An exploration of zero-click attack surface for the popular video conferencing solution Zoom has yielded two previously undisclosed security vulnerabilities that could have been exploited to crash the service, execute malicious code, and even leak arbitrary areas of its memory.
Dark Reading
JANUARY 21, 2022
The acceleration of the digital transformation resulted in a surge of online transactions, greater adoption of digital payments, and increased fraud
CyberSecurity Insiders
JANUARY 18, 2022
Winter Olympics 2022 that are scheduled to be held in Beijing from next month i.e. in between February 4th to February 22nd, 2022 is in news for wrong reasons.
We Live Security
JANUARY 20, 2022
Think your email may have been hacked? Here are the signs to look for, how account takeover attacks commonly occur, and how to recover your account and avoid falling victim again. The post How to know if your email has been hacked appeared first on WeLiveSecurity. How To
Let's personalize your content