US Government Sites Give Bad Security Advice
Krebs on Security
MARCH 25, 2020
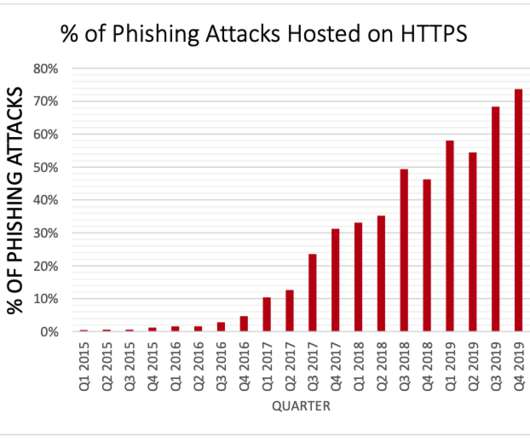
Many U.S. government Web sites now carry a message prominently at the top of their home pages meant to help visitors better distinguish between official U.S. government properties and phishing pages. Unfortunately, part of that message is misleading and may help perpetuate a popular misunderstanding about Web site security and trust that phishers have been exploiting for years now.









































Let's personalize your content