Top Cybersecurity Trends to Watch Out For in 2025
Centraleyes
DECEMBER 16, 2024
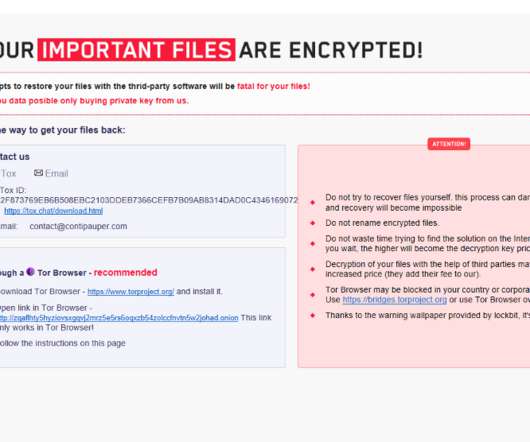
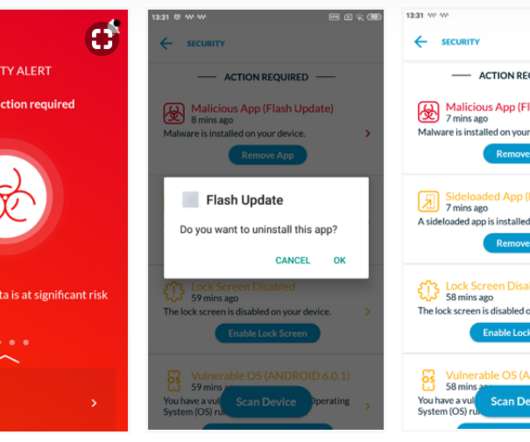
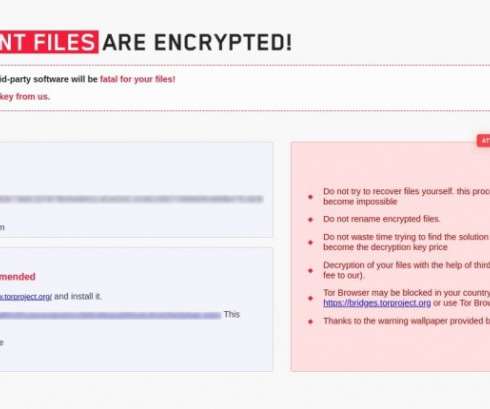
Attackers are becoming more organized, with ransomware-as-a-service (RaaS) operations providing easy access to malicious tools for even novice cybercriminals. Current cybersecurity trends show that attackers are now targeting critical infrastructure, healthcare, and financial services, leading to massive disruptions.









































Let's personalize your content