Building a secure and scalable multi-cloud environment with Cisco Secure Firewall Threat Defense on Alkira Cloud
Cisco Security
FEBRUARY 2, 2023
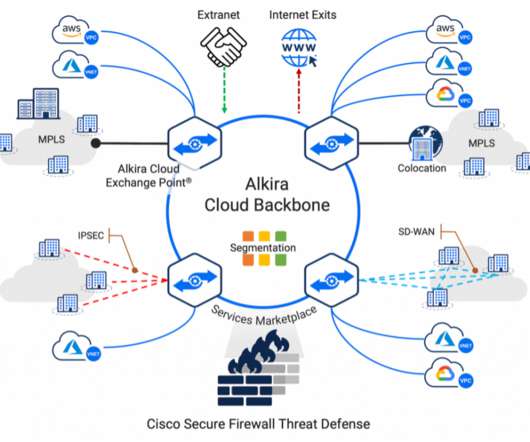
Cisco Secure Firewall Threat Defense Virtual provides unmatched security controls such as stateful firewalling, Snort3 IPS, URL filtering, malware defense, application visibility and control, and more. Customers can seamlessly deploy and insert Secure Firewall in their Alkira Cloud Exchange Points (CXP).













































Let's personalize your content