Inside the Massive Alleged AT&T Data Breach
Troy Hunt
MARCH 18, 2024
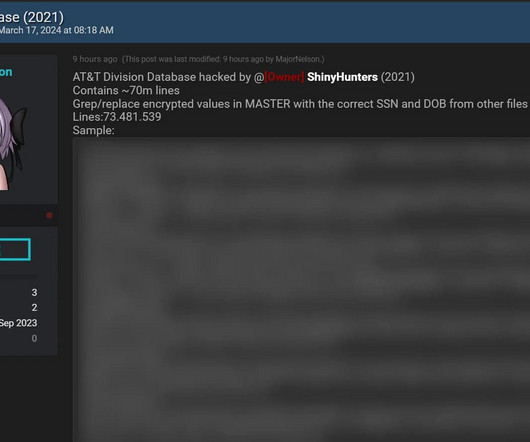
What it boils down to is in August 2021, someone with a proven history of breaching large organisations posted what they claimed were 70 million AT&T records to a popular hacking forum and asked for a very large amount of money should anyone wish to purchase the data. For my part, I've got 4.8M















































Let's personalize your content