Data Security: Think Beyond the Endpoint
Dark Reading
MAY 20, 2019
A strong data protection strategy is essential as data moves across endpoints and in the cloud.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 endpoint-security data-security-think-beyond-the-endpoint
endpoint-security data-security-think-beyond-the-endpoint 
Dark Reading
MAY 20, 2019
A strong data protection strategy is essential as data moves across endpoints and in the cloud.

The Last Watchdog
JULY 1, 2022
This raises the concerns of corporate data security in remote working that still stand as a key challenge that organizations are trying to navigate, workforce productivity being the second. Managing endpoints securely . Related: Deploying human sensors. Fragmentation dilemma .
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Cisco Security
JULY 27, 2022
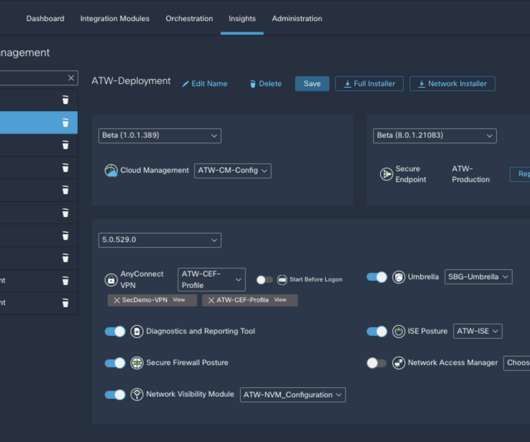
We’re excited to announce Cisco Secure Client, formerly AnyConnect, as the new version of one of the most widely deployed security agents. As the unified security agent for Cisco Secure , it addresses common operational use cases applicable to Cisco Secure endpoint agents. We’d love to hear what you think.
Anton on Security
DECEMBER 15, 2022
In recent weeks, I did two fun webinars related to Security Operations, and there was a lot of fun Q&A. For extra fun, I had ChatGPT answer some of them, to see if it can replace me :-) So, first, ISACA webinar “Modernize Your SOC for the Future” focused on our Autonomic Security Operations vision.

The Last Watchdog
FEBRUARY 28, 2022
However, APIs have gained traction so rapidly and deeply that not nearly enough attention has been paid to the associated security shortcomings. Many organizations, SMBs and enterprises alike, do not understand the scope and scale of their deployments of APIs, much less how to go about effectively securing their APIs. API complexity.

Malwarebytes
OCTOBER 1, 2023
New data destruction tactics in ransomware attacks. This use of dual ransomware variants resulted in a combination of data encryption, exfiltration, and financial losses from ransom payments. This use of dual ransomware variants resulted in a combination of data encryption, exfiltration, and financial losses from ransom payments.

Malwarebytes
APRIL 10, 2024
A new ransomware group, RansomHub, has listed the organisation as a victim on its dark web leak site, saying it has 4 TB of “highly selective data,” which relates to “all Change Health clients that have sensitive data being processed by the company.”

Malwarebytes
OCTOBER 17, 2023
” White House Deputy National Security Adviser Anne Neuberger said ransomware payment bans have been a topic of discussion among members of the CRI, and she noted that several other countries have also raised the issue, but no decisions have been made. The reasoning is very understandable.

The Last Watchdog
FEBRUARY 7, 2023
Using legitimate services and compromised corporate email addresses became a norm and is likely to continue in 2023 and beyond. Another report by Vade completed last year found that 87 percent of respondents agreed their organization could take the threat from email security more seriously. This is a harmful misconception.

Malwarebytes
APRIL 10, 2024
A new ransomware group, RansomHub, has listed the organisation as a victim on its dark web leak site, saying it has 4 TB of “highly selective data,” which relates to “all Change Health clients that have sensitive data being processed by the company.”

Cisco Security
MAY 19, 2021
We set out with the goal to streamline our customers’ operations with increased visibility across their security portfolio, provide out-of-the-box integrations, powerful security analytics, and automated workflows to speed threat detection and response. Cisco SecureX: Year 2. at RSA 2020!

CyberSecurity Insiders
FEBRUARY 28, 2023
No one likes to think their company might be hit by a cyber attack or breach, but the truth is cybercrime is one of the biggest threats your organization can face. If you suffer a breach, the loss of data is only the first of many issues you will be facing. Then we went and found them for you.
eSecurity Planet
APRIL 5, 2022
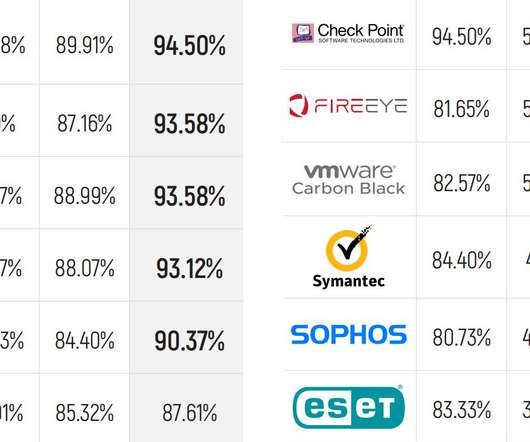
MITRE Engenuity has released the latest round of its ATT&CK endpoint security evaluations, and the results show some familiar names leading the pack with the most detections. MITRE doesn’t score results or try to say who “won,” and instead just provides the raw data. MITRE Methodology and Adversaries.

The Last Watchdog
NOVEMBER 14, 2022
Matter certified smart home devices will respond reliably and securely to commands from Amazon Alexa , Google Assistant , Apple HomeKit or Samsung SmartThings. Think of it: consumers will be able to control any Matter appliance with any iOS or Android device. This time we drilled down on the security pedigree of Matter 1.0.

Cisco Security
FEBRUARY 24, 2022
Security posture management challenges are driven by the growing attack surface. Meanwhile, security teams are also concerned about recent cybersecurity issues including MS Exchange vulnerabilities and the SolarWinds hack. About the report: Understanding security hygiene trends.

Malwarebytes
JUNE 20, 2023
The incident, first discovered on June 6th , involved the likely theft of data by an unauthorised party. The University has not confirmed if ransomware was used specifically, or if the attackers were only interested in stealing data. They, however, value money about the privacy and security of their students and employees.

eSecurity Planet
DECEMBER 13, 2021
Germany-based G Data CyberDefense released software designed to trick the STOP ransomware variant into believing that a targeted system has already been compromised and keeping it from encrypting files after the device has been infected. So I guess STOP thinks those files were successfully encrypted and hence renames them.”.

Malwarebytes
JULY 14, 2023
Chainalysis, a blockchain research firm, looked at data from monitored cryptocurrency wallets, concluding that around $449 million has been taken from victims in the last six months. Well, this is the practice of targeting large, financially well-off corporations in order to secure the biggest possible payouts.

IT Security Guru
MARCH 6, 2024
Cybersecurity threats are evolving at an unprecedented pace, posing significant challenges to Security Operations (SecOps) teams worldwide. Proactive Threat Management The cornerstone of a robust security strategy is not just to react to threats but to preempt them.

Cisco Security
MAY 11, 2022
As you start planning your RSAC and Cisco Live 2022 experiences, we invite you to explore the progress we have made in offering radically simple security with a platform approach that is transformative to the industry and for our customers. ” Key highlights to explore: Cisco Secure (Booth N6045). Beyond XDR with Cisco SecureX.

Cisco Security
NOVEMBER 18, 2021
On May 12, 2021, the president of the United States released an executive order on cyber security. As both public and private organizations look to comply with the order, many are wondering how to identify and fill the gaps within their security stack. See figure 1]. While the term NDR is relatively new, the technology is not.

Malwarebytes
AUGUST 25, 2023
Even so, they were able to steal close to $126,000 from five victims by abusing the SIM data used to secure their cryptocurrency accounts. You would think someone in this situation would steer clear of trouble. Kurtaj had his personal data leaked online , and had to be moved into a secure location for his own safety.

Malwarebytes
AUGUST 28, 2023
million people's personal data may be at risk, after the company suffered a ransomware attack earlier in the year. Certain files in the PurFoods network were encrypted, and investigators also noticed tools present which can be used for data exfiltration. An organisation that provides home delivery meals has revealed that around 1.2

SC Magazine
MAY 11, 2021
Researchers at Intezer released details behind a previously undisclosed vulnerability that could allow Microsoft Azure users with low-level privileges to leak private data from any virtual machine extension plugged into their cloud environment. Photo by Jeenah Moon/Getty Images).
Cisco Security
FEBRUARY 28, 2022
In its Hype Cycle for Security Operations, Gartner has defined Cyber Assets Attack Surface Management (CAASM) as “an emerging technology focused on enabling security teams to solve persistent asset visibility and vulnerability challenges”. This is where Secure Cloud Insights (SCI) steps in.

McAfee
DECEMBER 22, 2021
Organisations preparing to defend against this threat needs to think beyond the initial access vector. What the vulnerability allows a threat actor to do is initially only connect to a remote endpoint and establish a beachhead. The impact on organisations varies between resource takeover, denial of service or data theft.

eSecurity Planet
AUGUST 22, 2023
Remote access security is critical for protecting increasingly distributed work environments, ensuring that only authorized users can access your valuable information regardless of their location. The technologies for secure remote access can range from VPNs and multi-factor authentication to more advanced access and zero trust controls.

The Last Watchdog
MAY 11, 2021
By patiently slipping past the best cybersecurity systems money can buy and evading detection for 16 months, the perpetrators of the SolarWinds hack reminded us just how much heavy lifting still needs to get done to make digital commerce as secure as it needs to be. Related: DHS launches 60-day cybersecurity sprints. Advanced cloaking.

CyberSecurity Insiders
APRIL 8, 2022
By Steve Moore, Chief Security Strategist, Exabeam. When you take a step back and consider these statistics, you will quickly realize the gravity of what is at stake for organizations when it comes to effectively securing their confidential information – and that there is still a lot more to be done to combat this growing trend.

Cisco Security
JANUARY 21, 2022
In subsequent posts we are diving deeper into different Cisco Secure detection technologies and how their respective detections can be prioritised, promoted to SecureX as incidents and extended. For example “the PCI server just uploaded a lot of data to an external server” is very different than “10.10.10.10 An anomaly observation.

SecureWorld News
AUGUST 23, 2023
Amidst an environment of ever-evolving cyber threats, there is a strong need to progress how the industry approaches cyber protection for businesses to better equip security leaders during a period of staffing shortages and burnout. Here are some comments on the cyber risk landscape from cybersecurity vendor experts.

SecureWorld News
JULY 28, 2020
What does the data reveal about your employees and how they are thinking about cybersecurity right now? And worries are a little higher when it comes to personal consequences: 59%: Exposure of personal data to third parties. 55%: Personal financial loss due to unauthorized access to pay or retirement data.

Malwarebytes
JUNE 23, 2023
Just some of these tools include: Cobalt Strike : A legitimate commercial pen test to assess network security and simulate advanced threat actor tactics. Just some of these tools include: Cobalt Strike : A legitimate commercial pen test to assess network security and simulate advanced threat actor tactics.

Malwarebytes
MAY 8, 2023
Nevertheless, the gang was seen last month exploiting vulnerabilities in PaperCut servers to steal corporate data. Once gaining initial access, Cl0p members sneakily deploy the TrueBot malware and a Cobalt Strike beacon to creep through the network, grabbing data along the way. “The viability may improve in the future.

Lenny Zeltser
AUGUST 23, 2023
Start by critically reviewing how you’ll spend the security funds; this involves broadening your perspective beyond security. This way of thinking about cybersecurity brings CISOs closer to the world of CIOs. To do this, you may need to work with the finance team to itemize the expenses allocated to security at your firm.

SiteLock
AUGUST 27, 2021
diplomacy and national security, with emphases on technology trends in cyberwarfare, cyberdefense, and cryptography. With more consumers and B2B enterprises conducting business in the cyber world, security threats are an increasing concern. This is not to be confused with GDPR , which governs general data protection.
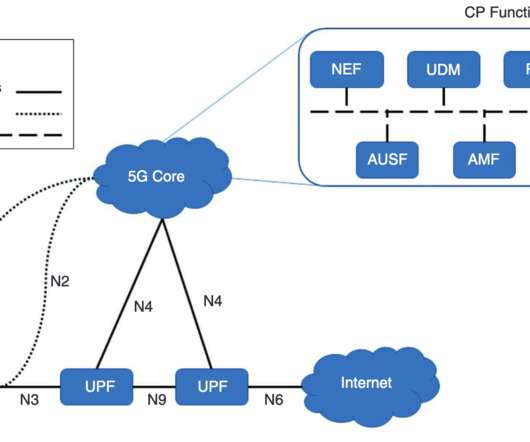
Adam Shostack
JULY 1, 2021
I think the report from a Threat Model Working Panel of the Enduring Security Framework of CIPAC, but then there’s language like “identified by the ESF and 5G TM working panel… (emphasis added)” which implies its separate. The data gathered by 5G? What are we working on? Is it the networks?

Herjavec Group
JUNE 25, 2021
Business leaders now have to re-assess their security toolbox and look for stronger protections in the new digital landscape of their companies. Whether you’re selling custom t-shirts on Shopify, or you’re the largest online retailer in the world, all businesses are vulnerable to data breaches and malware.
Security Boulevard
DECEMBER 15, 2022
In recent weeks, I did two fun webinars related to Security Operations, and there was a lot of fun Q&A. So, first, ISACA webinar “Modernize Your SOC for the Future” focused on our Autonomic Security Operations vision. The questions below are sometimes slighting edited for clarity, typos, etc.
Cisco Security
SEPTEMBER 28, 2021
It scrambles all the data on your device so you can’t access it. Initially, ransomware attackers simply left the locked data where it was. Cybersecurity affects all of us, but the industry uses complicated terms that make it hard to understand. For example, what is ransomware and how does it work? What does phishing mean?

SecureWorld News
JULY 23, 2020
On one hand, the rapid transition posed some serious cybersecurity challenges as companies scrambled to adapt and secure their networks and many endpoints. Further, it revealed that 85 percent of respondents agree that teleworking is here to stay—even beyond the pandemic.". On the other hand, employees are loving it.

Malwarebytes
MARCH 10, 2021
As per the link, it’s generally a lot harder to secure sound than vision. As per the link, it’s generally a lot harder to secure sound than vision. Either the hardware tinkering is beyond them, or their audio setup is a confusing mess of six audio devices and brand-specific audio controls. How does your Android phone work?

Malwarebytes
JANUARY 15, 2023
The school eventually realised that data had been stolen somewhere around the October 14, notifying the parents. Law enforcement are investigating, but this timeline of not knowing data had been exfiltrated for a week or two is sadly common. Special Educational Needs (SEN) data. Schools: A recurring target.
SC Magazine
JULY 13, 2021
Think of Insider Threat Management Programs (ITMPs) as a holistic focus on managing the risks that insiders pose to your corporate assets. It starts with a strong foundation: a unified mission that breaks down the traditional silos between “security” (personnel-focused) and “InfoSec” (network-focused IT).
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content