Applying Security Engineering to Prompt Injection Security
Schneier on Security
APRIL 29, 2025
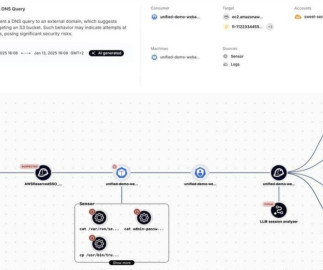
Rather than expecting AI to detect attacks, CaMeL implements established security engineering principles like capability-based access control and data flow tracking to create boundaries that remain effective even if an AI component is compromised. Research paper. Good analysis by Simon Willison.











Let's personalize your content