No Code / Low Code for Social Engineering
Security Boulevard
NOVEMBER 14, 2022
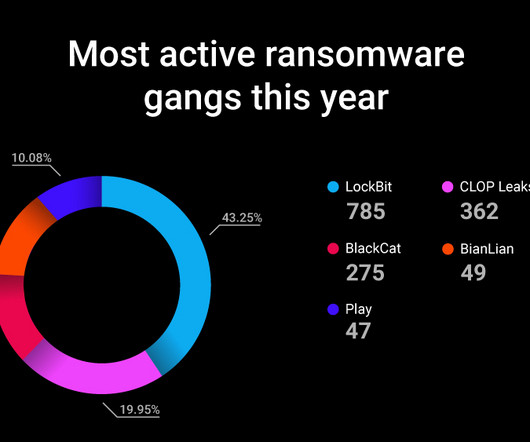
The conversation bounced around from the Silk Road, to recently seized bitcoin, to stolen passwords, to ways cyber criminals share software and information with each other. Data stolen in breaches, such as usernames and passwords, are widely available. Here’s what you can do to protect yourself and your team.Don't reuse passwords.
















































Let's personalize your content