CrowdStrike 2024 Global Threat Report: 6 Key Takeaways
Tech Republic Security
FEBRUARY 26, 2024
Identity-based and social engineering attacks still take center stage, according to the CrowdStrike 2024 Global Threat Report.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Tech Republic Security
FEBRUARY 26, 2024
Identity-based and social engineering attacks still take center stage, according to the CrowdStrike 2024 Global Threat Report.

Security Boulevard
MAY 18, 2023
Experts are worried that ChatGPT’s ability to source recent data about an organization could make social engineering and phishing attacks more effective than ever. The post When ChatGPT Goes Phishing appeared first on Security Boulevard.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
eSecurity Planet
OCTOBER 3, 2022
PuTTY, KiTTY, TightVNC, Sumatra PDF Reader, and the muPDF/Subliminal Recording software installer have been backdoored to perform a wide range of social engineering campaigns that started in April 2022. Using DLL hijacking, ZINC can schedule additional tasks and install malware on the compromised machines.

CyberSecurity Insiders
MAY 28, 2023
Malware Analysis: Explore malware types, their behavior, and the techniques used for analyzing and detecting them. Investigate malware’s propagation methods, evasion techniques, and methods for identifying and mitigating potential threats.
eSecurity Planet
SEPTEMBER 15, 2022
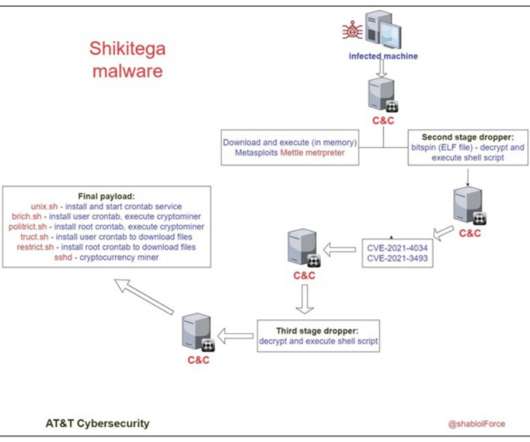
AT&T Alien Labs has discovered a new Linux malware that can be used for highly evasive attacks, as the infection has been designed for persistence and runs on practically all kinds of Linux devices. Researchers dubbed the malware “Shikitega.” Two of them regard the current user and the rest are for the root account.

The Last Watchdog
MARCH 4, 2024
Nonprofits can bolster their network security by insisting on strong login credentials. Ransomware: This attack involves criminals holding a network and its precious data hostage until the enterprise pays the demanded amount. Strengthen authentication. Lack of proper staff training is the biggest culprit in this case.

Security Boulevard
MAY 31, 2022
In April of 2013, CNN introduced the world to Shodan, a search engine for internet-connected devices, by publishing an article titled, Shodan: The scariest search engine on the Internet. The post Shodan: Still the Scariest Search Engine on the Internet?

Doctor Chaos
FEBRUARY 16, 2022
I recently came across a classic malware which I thought was long gone and forgotten. Rombertik is a self-destructing malware that has been making a lot of news. This malware leverages vulnerabilities through a Web browser’s operation of collecting user data from sites being visited by the victim. What We Learned.

Security Affairs
MAY 3, 2021
Malware Attacks Hackers and cybercriminals often launch malware attacks to achieve their malicious goals. Some malware attacks install tools like keyloggers to capture the keystrokes for stealing passwords or other sensitive information. They must educate their employees about cybersecurity, social engineering, and phishing.
eSecurity Planet
NOVEMBER 7, 2022
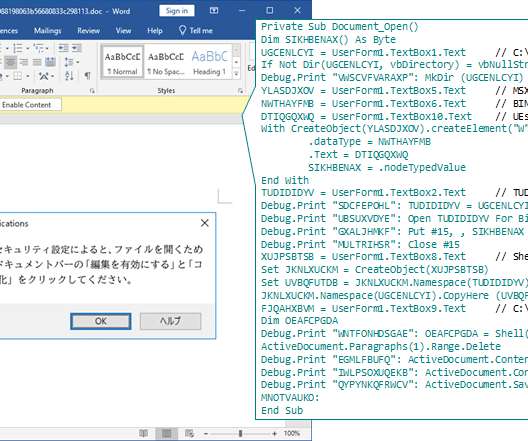
Kaspersky researchers recently found evidence of an advanced threat group continuously updating its malware to evade security products, similar to a release cycle for developers. The sophisticated malware was hidden in malicious Word file attachments. during their investigation. See the Best EDR Solutions.

Security Boulevard
MARCH 29, 2023
As attacks continue to evolve, harnessing AI and advanced social engineering techniques for increasingly sophisticated, stealthy attacks, many. The post We’ve Been Using Email Since 1971—It’s Time We Make it Secure appeared first on Security Boulevard. Email is one of the most important communication tools used today.

Security Boulevard
NOVEMBER 29, 2022
TikTok’s ‘Invisible Body’ challenge was too great an opportunity for malware scrotes to pass up: “You too can see you favorite TikTok star naked!”. The post Naked TikTok Girls = Malware Mayhem ? InvisibleFilter appeared first on Security Boulevard.

SC Magazine
APRIL 1, 2021
The attackers used a new cryptor to obfuscate the malware code they hid in seemingly legitimate files and evade detection from antivirus software. Secondly, it replaces much of the legwork that goes into a hacking operation with a simple and straightforward social engineering approach.

eSecurity Planet
AUGUST 3, 2023
In his blog post , Kelley shared a video from CanadianKingpin12 that suggests DarkBERT will go well beyond the social engineering capabilities of the earlier tools with new “concerning capabilities.”

Security Boulevard
JANUARY 17, 2022
Ukraine is again under malware attack. The post ‘Russian’ Wiper Malware: ‘Prelude to war’ in Ukraine appeared first on Security Boulevard. And the tactics look strikingly similar to 2017’s NotPetya hack by the Russian GRU.

Security Affairs
SEPTEMBER 15, 2022
Threat actors used employees’ publicly-available Personally Identifiable Information (PII) and social engineering techniques to impersonate victims and obtain access to files, healthcare portals, payment information, and websites. Well-maintained anti-virus and anti-malware software may prevent commonly used attacker tools.

Security Boulevard
OCTOBER 26, 2021
Social engineering schemes continue to flourish, making their way into company inboxes with the intent to mislead employees into downloading malicious software. These schemes appear fraudulent to those familiar with phishing.

eSecurity Planet
FEBRUARY 21, 2023
Blue teams consist of security analysts, network engineers and system administrators. The team may be divided into sub-teams depending on the type of security controls it is responsible for, such as network security, endpoint security, or the security operations center (SOC).

Security Boulevard
MAY 14, 2021
HelpSystems this week acquired both Beyond Security, a provider of a cloud-based service for scanning applications for network and network or application vulnerabilities, and Agari, a provider of a software-as-a-service (SaaS) platform that employs data science to help combat social engineering and phishing attacks.

CyberSecurity Insiders
JUNE 18, 2022
As more and more businesses increase the number of their digital assets and incorporate new technology to operate, they turn their attack surface into an intricate network. Securing all the systems that include remote employees’ endpoint devices and multi-cloud environments has been a challenge. To Conclude.

Malwarebytes
MAY 23, 2023
Create policies to include cybersecurity awareness training about advanced forms of social engineering for personnel that have access to your network. It is also important to repeat security awareness training regularly to keep your staff informed and vigilant. Drive-by-downloads. Malvertising. Prevent intrusions.

CyberSecurity Insiders
MAY 18, 2022
Not long ago, it was revealed that T-Mobile had been breached by bad actors who convinced employees to switch their SIM cards to let them bypass two-factor identification — reminding us how effective social engineering can still be. When malware first breaches a network, it doesn’t make its presence known right away.

Security Boulevard
APRIL 17, 2023
It’s Help|About Time: Chrome’s “V8” JavaScript engine has high-severity vuln. The post Drop Everything: Update Chrome NOW — 0-Day Exploit in Wild appeared first on Security Boulevard. Scrotes already exploiting it.

SecureWorld News
MARCH 11, 2022
Famed hacker Kevin Mitnick learned early on to use emotion to manipulate and socially engineer his targets. At the time, his targets were typically sysadmins, and the social engineering started with a phone call. KnowBe4 Security Awareness Advocate Erich Kron is an expert in this space. You could lose your data.'.

SC Magazine
FEBRUARY 17, 2021
The remote work trend, along with an expanding distributed workforce, has complicated network security at many businesses. The Zscaler report also found: 93% of companies surveyed have deployed VPN services, despite 94% of those surveyed admitting that they are aware that cybercriminals are exploiting VPNs to access network resources.

eSecurity Planet
AUGUST 23, 2023
This method involves using emails, social media, instant messaging, and other platforms to manipulate users into revealing personal information or performing actions that can lead to network compromise, data loss, or financial harm. The likelihood that the target will respond to a message is increased by this personalization.

Security Boulevard
JUNE 5, 2023
Malware Déjà Vu: Perhaps as many as 87 million victims—maybe more. The post Chrome Extensions Warning — Millions of Users Infected appeared first on Security Boulevard.

Security Affairs
MARCH 10, 2020
In human-operated ransomware attack scenario, attackers use stolen credentials, exploit misconfiguration and vulnerabilities to access target networks, attempt to escalate privileges and move laterally, and deliver malware and exfiltrate data. ” reads the post published by Microsoft.

eSecurity Planet
AUGUST 22, 2022
180 to download additional malware and deletes itself after installation. SocGholish (aka Fake Updates) is a JavaScript-based malware that masquerades as a legitimate browser update delivered to victims via compromised websites. Security Awareness Training Improvements Coming. “As org and IP 176[.]10[.]124[.]180

Security Boulevard
DECEMBER 17, 2021
Researchers have reverse engineered NSO group’s recent zero-click iPhone exploit. The post NSO Zero-Click Exploit: Turing-Complete CPU in Image File appeared first on Security Boulevard. And it’s a doozy.

Security Boulevard
FEBRUARY 20, 2023
This time, the perps were redirecting legit websites to malware. The post GoDaddy Hosting Hacked — for FOURTH Time in 4 Years appeared first on Security Boulevard. GoDaddy’s web hosting service breached yet again.

Security Boulevard
NOVEMBER 22, 2023
Flash drive sharing malware escapes Україна. The post ‘LitterDrifter’ Russian USB Worm Leaks from Ukraine War Zone appeared first on Security Boulevard. FSB APT USB VBS LNK DLL: WTH? Gamaredon fingered as perps.

Malwarebytes
JUNE 7, 2021
An ethical hacker can be someone who tests their own computer’s network defenses to develop their knowledge of computer software and hardware or a professional hired to test and enhance system security. Security careers related to ethical hacking are in-demand. Malware analysts are a good example.

Security Boulevard
DECEMBER 5, 2022
A new wiper malware is destroying data on Russian government PCs. The post Russia Hit by New ‘CryWiper’ — Fake Ransomware appeared first on Security Boulevard. Dubbed CryWiper, it pretends to be ransomware.

eSecurity Planet
MARCH 17, 2023
Whether you’re operating a global enterprise network or a small family business, your network’s security needs to be optimized with tools, teams, and processes to protect customer data and valuable business assets. Many of these tools protect resources connected to networks, thus shutting down threats as early as possible.

eSecurity Planet
FEBRUARY 16, 2021
Malware, short for “malicious software,” is any unwanted software on your computer that, more often than not, is designed to inflict damage. Since the early days of computing, a wide range of malware types with varying functions have emerged. Rogue security software. Best Practices to Defend Against Malware.

Security Boulevard
AUGUST 3, 2021
Some Italian healthcare websites and their backroom systems have been wiped off the internet by malware. The post Italian Vaccine Sites Shut Down by Ransomware Thugs appeared first on Security Boulevard.

eSecurity Planet
MARCH 15, 2024
Here are the five query functions you can use: Network hacking: This function allows users to delve into network security, offering information about computer network vulnerabilities and threats. It discusses techniques like port scanning, packet sniffing, and exploiting flaws in network protocols.

Security Boulevard
JANUARY 12, 2022
The FBI issued a warning that a group of threat actors from the FIN7 cybercrime group has resorted to an old trick—mailing USB sticks loaded with BadUSB malware to companies. The post FBI Issues Warning on FIN7 USB Stick Exploit appeared first on Security Boulevard.

Security Boulevard
MAY 19, 2022
These variants of Vidar malware fetch the C2 configuration from attacker-controlled social media channels hosted on Telegram and Mastodon network. These binaries hosted on GitHub, distribute Vidar malware using similar tactics of abusing social media channels for C2 communication. Technical Analysis. Version: 51.9.

Malwarebytes
JUNE 8, 2022
Malware authors and distributors are following the ebbs and flow of the threat landscape. For some reason the threat actors are reusing the same servers in Russia and naming their malvertising gates after different ad networks. Security researcher @na0_sec saw the “MakeMoney gate”, named after the domain makemoneywithus[.]work

Security Boulevard
FEBRUARY 24, 2021
When the pandemic struck, online bad actors took it as an opportunity to double-down on their attacks through ransomware, malware, and social engineering. SASE network architecture, like multi-cloud storage, brings multiple systems together to link security solutions for the greatest effect.

Security Boulevard
APRIL 29, 2024
The post South Korean iPhone Ban: MDM DMZ PDQ appeared first on Security Boulevard. MDM Hindered: Android phones are still OK; this is Samsung’s home, after all.

eSecurity Planet
SEPTEMBER 10, 2021
The following sections speak to how ransomware can affect organizations with backup strategies in place, the implications of advanced malware , and why the type of backup solution matters. Malware constantly evolves to match advancing cybersecurity standards and solutions, and ransomware is no exception. Data Exfiltration.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content