Amazon discloses employee data breach after May 2023 MOVEit attacks
Security Affairs
NOVEMBER 11, 2024
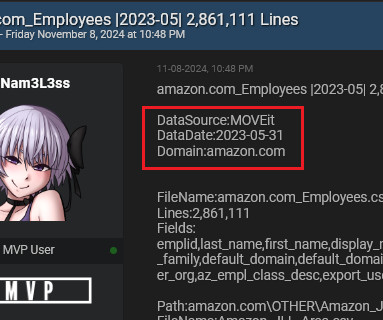
million records containing employee data on the hacking forum BreachForums. Compromised data includes names, contact information, building locations, email addresses, and more. Exposed data did not include Social Security numbers or financial information. A threat actor using the handle Nam3L3ss leaked over 2.8

































Let's personalize your content