Critical Actions Post Data Breach
SecureWorld News
DECEMBER 30, 2024
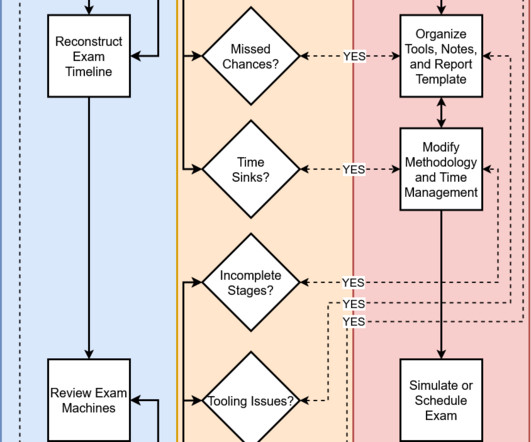
ISO 22317: Focuses on Business Impact Analysis (BIA), detailing the processes for identifying and evaluating the impact of different events on business operations. Collect and safeguard critical artifacts such as event logs, system logs, and authentication records from corporate systems.


















































Let's personalize your content