Telecommunications: A Case Study
Approachable Cyber Threats
MARCH 9, 2023
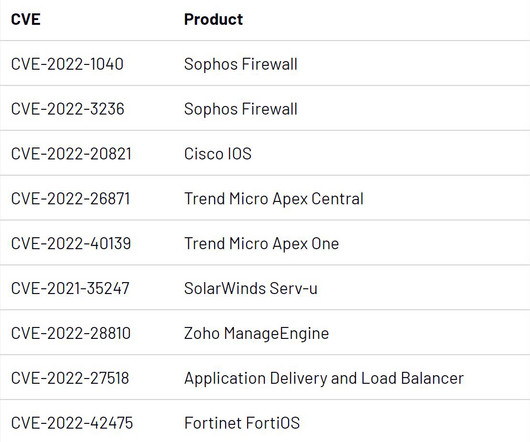
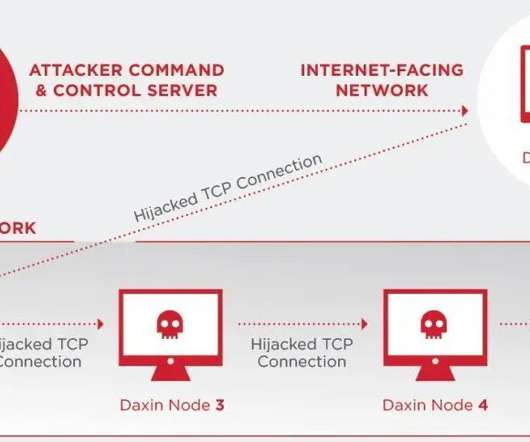
Category Awareness, News, Case Study As one of the world’s fastest-growing industries, telecommunication has become a highly vulnerable target for cybersecurity threats. In short, telecommunications (telecom) is a fundamental and critical component of our global infrastructure. What can be done? Read more of the ACT




























Let's personalize your content