Kalay cloud platform flaw exposes millions of IoT devices to hack
Security Affairs
AUGUST 17, 2021
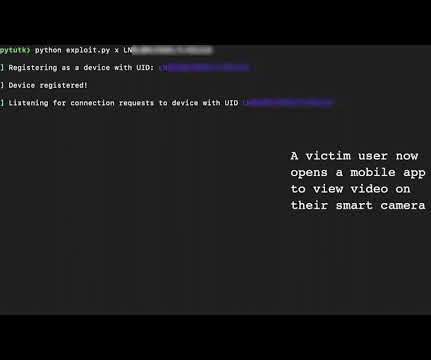
The identifier could be obtained via social engineering. The attacker would also need to obtain Kalay UIDs through social engineering or other vulnerabilities in APIs or services that return Kalay UIDs. This varies from device to device but typically is used for device telemetry, firmware updates, and device control.”














Let's personalize your content