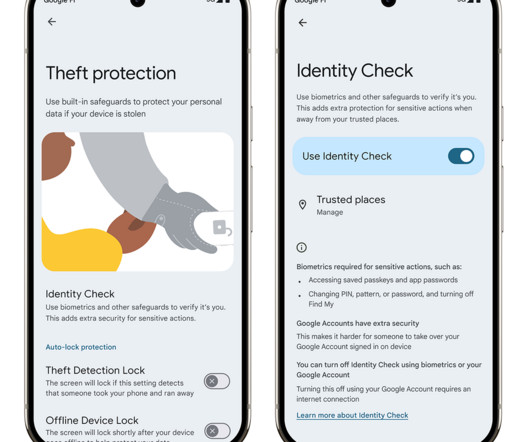
Android enhances theft protection with Identity Check and expanded features
Google Security
JANUARY 23, 2025
But a stolen device in the wrong hands can expose sensitive data, leaving you vulnerable to identity theft, financial fraud and privacy breaches. This is why we recently launched Android theft protection , a comprehensive suite of features designed to protect you and your data at every stage before, during, and after device theft.














































Let's personalize your content