Phishing-as-a-Service Rockstar 2FA continues to be prevalent
Security Affairs
NOVEMBER 29, 2024
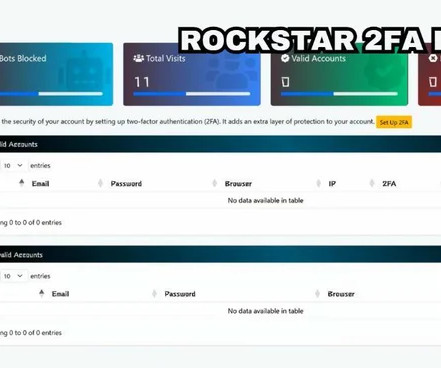
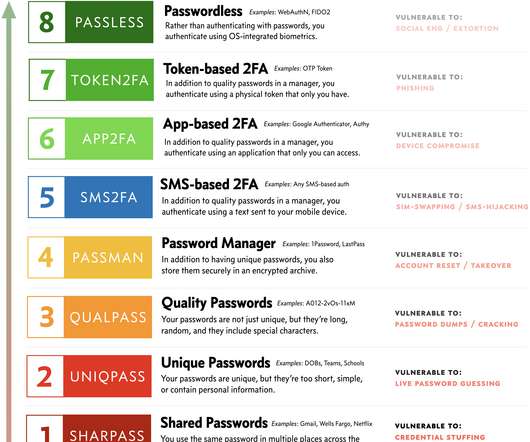
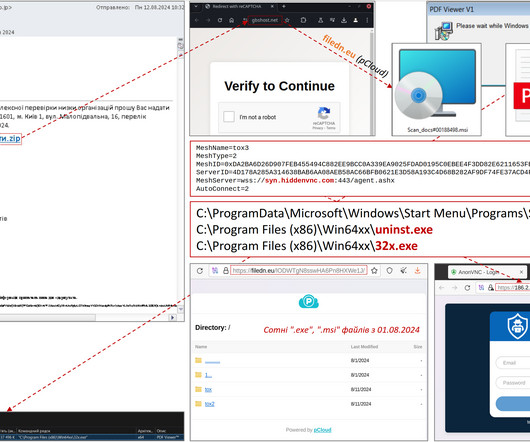
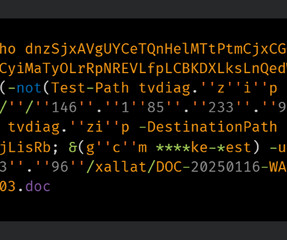
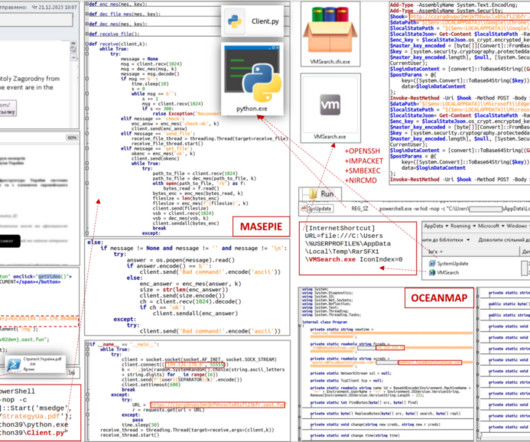
Phishing tool Rockstar 2FA targets Microsoft 365 credentials, it uses adversary-in-the-middle (AitM) attacks to bypass multi-factor authentication. Trustwave researchers are monitoring malicious activity associated with Phishing-as-a-Service (PaaS) platforms, their latest report focuses on a toolkit called Rockstar 2FA.



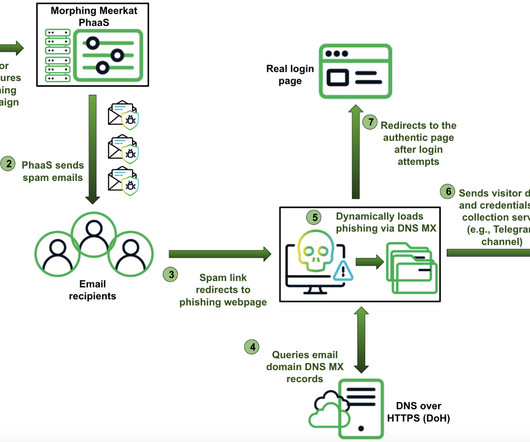
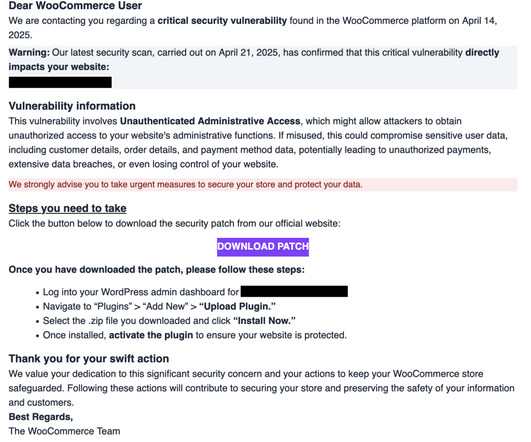
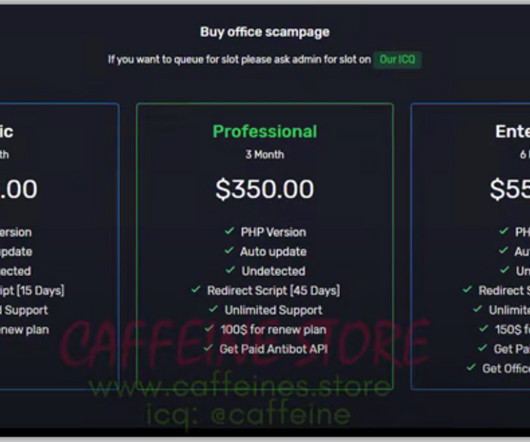
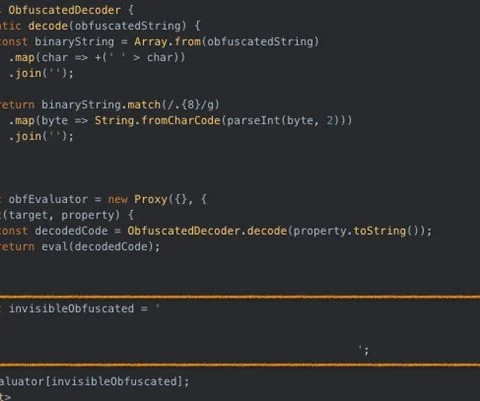

























Let's personalize your content